1. What are some password basics?
Most accounts on a computer system usually have some method of restricting access to that account, usually in the form of a password. When accessing the system, the user has to present a valid ID to use the system, followed by a password to use the account. Most systems either do not echo the password back on the screen as it is typed, or they print an asterisk in place of the real character.
On most systems,the password is typically ran through some type of algorithm to generate a hash. The hash is usually more than just a scrambled version of the original text that made up the password, it is usually a one-way hash. The one-way hash is a string of characters that cannot be reversed into its original text. You see, most systems do not "decrypt" the stored password during authentication, they store the one-way hash. During the login process, you supply an account and password. The password is ran through an algorithm that generates a one-way hash. This hash is compared to the hash stored on the system. If they are the same, it is assumed the proper password was supplied.
Cryptographically speaking, some algorithms are better than others at generating a one-way hash. The main operating systems we are covering here -- NT, Netware, and Unix -- all use an algorithm that has been made publically available and has been scrutinized to some degree.
To crack a password requires getting a copy of the one-way hash stored on the server, and then using the algorithm generate your own hash until you get a match. When you get a match, whatever word you used to generate your hash will allow you to log into that system. Since this can be rather time-consuming, automation is typically used. There are freeware password crackers available for NT, Netware, and Unix.
2. Why protect the hashes?
If the one-way hashes are not the password itself but a mathematical derivative, why should they be protected? Well, since the algorithm is already known, a password cracker could be used to simply encrypt the possible passwords and compare the one-way hashes until you get a match. There are two types of approaches to this -- dictionary and brute force.
Usually the hashes are stored in a part of the system that has extra security to limit access from potential crackers.
3. What is a dictionary password cracker?
A dictionary password cracker simply takes a list of dictionary words, and one at a time encrypts them to see if they encrypt to the one way hash from the system. If the hashes are equal, the password is considered cracked, and the word tried from the dictionary list is the password.
Some of these dictionary crackers can "manipulate" each word in the wordlist by using filters. These rules/filters allow you to change "idiot" to "1d10t" and other advanced variations to get the most from a word list. The best known of these mutation filters are the rules that come with Crack (for Unix). These filtering rules are so popular they have been ported over to cracking software for NT.
If your dictionary cracker does not have manipulation rules, you can "pre-treat" the wordlist. There are plenty of wordlist manipulation tools that allow all kinds of ways to filter, expand, and alter wordlists. With a little careful planning, you can turn a small collection of wordlists into a very large and thorough list for dictionary crackers without those fancy word manipulations built in.
4. What is a brute force password cracker?
A brute force cracker simply tries all possible passwords until it gets the password. From a cracker perspective, this is usually very time consuming. However, given enough time and CPU power, the password eventually gets cracked.
Most modern brute force crackers allow a number of options to be specified, such as maximum password length or characters to brute force with.
5. Which method is best for cracking?
It really depends on your goal, the cracking software you have, and the operating system you are trying to crack. Let's go through several scenarios.
If you remotely retrieved the password file through some system bug, your goal may be to simply get logged into that system. With the password file, you now have the user accounts and the hashes. A dictionary attack seems like the quickest method, as you may simply want access to the box. This is typical if you have a method of leveraging basic access to gain god status.
If you already have basic access and used this access to get the password file, maybe you have a particular account you wish to crack. While a couple of swipes with a dictionary cracker might help, brute force may be the way to go.
If your cracking software does both dictionary and brute force, and both are quite slow, you may just wish to kick off a brute force attack and then go about your day. By all means, we recommend a dictionary attack with a pre-treated wordlist first, followed up by brute force only on the accounts you really want the password to.
You should pre-treat your wordlists if the machine you are going to be cracking from bottlenecks more at the CPU than at the disk controller. For example, some slower computers with extremely fast drives make good candidates for large pre-treated wordlists, but if you have the CPU cycles to spare you might want to let the cracking program's manipulation filters do their thing.
A lot of serious hackers have a large wordlist in both regular and pre-treated form to accommodate either need.
6. What is a salt?
To increase the overhead in cracking passwords, some algorithms employ salts to add further complexity and difficulty to the cracking of passwords. These salts are typically 2 to 8 bytes in length, and algorithmically introduced to further obfuscate the one-way hash. Of the major operating systems covered here, only NT does not use a salt. The specifics for salts for both Unix and Netware systems are covered in their individual password sections.
Historically, the way cracking has been done is to take a potential password, encrypt it and produce the hash, and then compare the result to each account in the password file. By adding a salt, you force the cracker to have to read the salt in and encrypt the potential password with each salt present in the password file. This increases the amount of time to break all of the passwords, although it is certainly no guarantee that the passwords can't be cracked. Because of this most modern password crackers when dealing with salts do give the option of checking a specific account.
7. What are the dangers of cracking passwords?
The dangers are quite simple, and quite real. If you are caught with a password file you do not have legitimate access to, you are technically in possession of stolen property in the eyes of the law. For this reason, some hackers like to run the cracking on someone else's systems, thereby limiting their liability. I would only recommend doing this on a system you have a legitimate or well-established account on if you wish to keep a good eye on things, but perhaps have a way of running the cracking software under a different account than your own. This way, if the cracking is discovered (as it often is -- cracking is fairly CPU-intensive), it looks to belong to someone else. Obviously, you would want to run this under system adminstrator priviledges as you may have a bit more control, such as assigning lower priority to the cracking software, and hiding the results (making it less obvious to the real administrator).
Being on a system you have legit access to also allows you better access to check on the progress. Of course, if it is known you are a hacker, you'll still be the first to be blamed whether the cracking software is yours or not!
Running the cracking software in the privacy of your own home has the advantage of allowing you to throw any and all computing power you have at your disposal at a password, but if caught (say you get raided) then there is little doubt whose cracking job is running. However, there are a couple of things you can do to protect yourself: encrypt your files. Only decrypt them when you are viewing them, and wipe and/or encrypt them back after you are done viewing them.
8. Is there any way I can open a password-protected Microsoft Office document?
Certainly! There are plenty of commercial programs that will do this, but we give props to Elcomsoft for fighting the DMCA. 30-day trial versions are available here
Password Hacking
BlazingTools Perfect Keylogger Lite (Keylogger)
BlazingTools Perfect Keylogger Lite:
Description:
Do you want to know what your buddy or colleague is typing? May be you want to control your family members - what are they doing on your computer? Some applications of the keylogger: - Monitor children's activity for parents - Monitor what programs opened and when - Recall what you wrote some time ago - Special purposes Features: - Invisible in Task Manager List - Logging texts typed in every application (including passwords and other hidden texts) - Log file is encrypted and can be protected with a password - Easy log viewing and management - Export log to HTML format - Possibility to specify target applications - Supports all Windows versions, including Windows XP - Very easy to use - Free version.
Download
Keyboard Spectator Free (Keylogger)
Keyboard Spectator Free
Description:
Keyboard Spectator is a multifunctional keyboard tracking software (a.k.a. key logger) that is widely used by both regular users and IT security specialists. The reason for such popularity is that this program does not just record keystrokes; it is capable of recording language specific characters (ex. umlauts), date and time certain window was initiated as well as the caption of that window. Thus, this software combines two very important qualities - it records all typed data, so that you won't lose it when your computer unexpectedly crashes, and it keeps the record of all keyboard activity. It allows you to monitor your children's activity at home or to make sure your employees do not use company's computers inappropriately.
Download
Ardamax Keylogger Lite (Keylogger)
Ardamax Keylogger Lite
Description
Ardamax Keylogger Lite is a small, freeware keylogger that captures users activity and saves it to a logfile. The logfile can be viewed as a text or web page. Use this tool to find out what is happening on your computer while your away, maintain a backup of your typed data automatically or use it to monitor your kids.
Download
Quick Keylogger (Keylogger)
Quick Keylogger
Description
WideStep Software presents light and affordable monitoring utility Quick Keylogger that supports 64 bit Windows as well as other OS. Simple download and deployment guarantees a smooth start of your work with the optimal set of features: keystrokes, websites and other monitoring options. Simple but clear HTML reports make Quick Keylogger a great solution for everyone. Quick Keylogger will save keystrokes by application, date and time, it will capture absolutely all keystrokes, all buttons pressed in your system. Unfortunately unlike Elite Keylogger it is not that invisible to anti-keyloggers and anti-viruses. Designed for Windows 9x, Windows XP and Windows Vista Quick Keylogger offers you stability and simplicity with the most usable number of features. Quick Keylogger works seemlessly in the background and you are the only one who knows the password to view the logs. Quick Keylogger is equipped with a calendar that lets you sort and review logs by specific dates and time. All recorded sessions are combined by user, date, month, and time. Quick Keylogger is easy-to-use, very simple and small (instant free download) tool, which you can carry on a floppy disk drive for your mobility and fast response.
Download
Hack BSNL Broadband For Speed
If you are a BSNL broadband user, chances are that you are facing DNS issues for the last few weeks or so. Their DNS servers are just unresponsive. The lookup takes a long duration and many times just time out. The solution? Use third party DNS servers or run your own one like djbdns. The easiest options is to use OpenDNS. Just reconfigure your network to use the following DNS servers:
208.67.222.222
208.67.220.220
Detailed instructions specific to your router are available in the OpenDNS website itself. After I reconfigured my Linksys router to use the above 2 IP addresses, my DNS problems just vanished! Other ‘freebies’ that come with OpenDNS are phishing filters and automatic URL correction. Even if your service provider’s DNS servers are working fine, you can still use OpenDNS just for these two special features.
Bypassing Vista SP1 Windows Genuine Advantage
The fact that Microsoft has relaxed its antipiracy mechanism built into Windows Vista concomitantly with the release of Service Pack 1 failed to stop hackers from providing a crack for the latest version of Windows Genuine Advantage Validation.
Various reports point out that Genuine Advantage Validation and Notifications versions 1.7.69.1 (1.7.0069.1) and 1.7.69.2 released in March 2008, following the March 18 availability of Windows Vista SP1 through Windows Update and the Microsoft Download Center, have been cracked.
The workaround is designed to be integrated with pirated copies of Windows XP and Windows Vista in order to render useless the WGA Validation mechanism. According to the reports, applying the WGA crack will permit users of counterfeit versions of Windows to access and download items from Windows Update, Microsoft Download Center and Microsoft Update. The pirated operating systems with the cracked WGA will pass all validations on Microsoft's websites and offer anything from updates to applications that are restricted to users of genuine operating systems only.
With the release of Windows Vista SP1, Microsoft has scrapped the Reduced Functionality Mode kill switch in its latest operating system. Users of pirated Vista, just as those of XP and Windows Server 2008 will only be informed of the fact that their operating system is no longer genuine. However, pirated versions of Windows are automatically blocked from downloading certain free applications as well as all updates except those labeled Critical. The WGA crack is designed to fix that.
"After the activation grace period has been exceeded the next logon will present the user with a message that directs the customer to activate that copy of Windows. That dialog includes a fifteen second delay before it can be dismissed. If they want to skip activation at that time they can wait for the fifteen seconds and choose "Activate Later" .
But the new story is different.That is Vista SP1 has been cracked successfully and it's possible to bypass the Windows Genuine Advantage to fool the OS to beleive it as genuine.The release of Service Pack 1 for Vista seems to put no combat against piracy.This crack is available for download on this site.
MORE INFORMATION ON THE CRACK(ACTIVATOR)
VistaSP1_1-Click Activator
Unlike the other cracks eg: Vista Loader 3.0.0.1(which has some known issues with dual booting systems) this crack has been designed to work on dual booting systems.
This crack has incorporated an automated installation process which makes it easy to install.You can select from 4 OEM Logos and licenses during installation and within a few seconds your copy will be activated.You can see the system activated upon restart.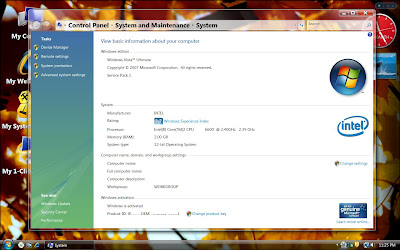
This crack also features the uninstallation process which most of the cracks lack the same.Using this is not necessary to carry out the manual uninstallation process.You can just uninstall the crack with a single click.
PLEASE FOLLOW THESE INSTRUCTIONS BEFORE APPLYING THIS CRACK.
1.YOU MUST HAVE FULL ADMINISTRATOR RIGHTS TO INSTALL THIS CRACK.
2.TURN OFF USER ACCOUNT CONTROL(UAC) BEFORE INSTALLING THIS CRACK.
3.THIS CRACK CURRENTLY WORKS ONLY WITH 32-BIT ULTIMATE EDITION OF WINDOWS VISTA.
4.EASY ONE CLICK ACTIVATOR.
5.YOU CAN ALSO USE THIS CRACK TO UNINSTALL THE ACTIVATOR.
ENJOY!!!
Here is the download link for the crack
DOWNLOAD
Please post your feedback through comments.










