1. What are some password basics?
Most accounts on a computer system usually have some method of restricting access to that account, usually in the form of a password. When accessing the system, the user has to present a valid ID to use the system, followed by a password to use the account. Most systems either do not echo the password back on the screen as it is typed, or they print an asterisk in place of the real character.
On most systems,the password is typically ran through some type of algorithm to generate a hash. The hash is usually more than just a scrambled version of the original text that made up the password, it is usually a one-way hash. The one-way hash is a string of characters that cannot be reversed into its original text. You see, most systems do not "decrypt" the stored password during authentication, they store the one-way hash. During the login process, you supply an account and password. The password is ran through an algorithm that generates a one-way hash. This hash is compared to the hash stored on the system. If they are the same, it is assumed the proper password was supplied.
Cryptographically speaking, some algorithms are better than others at generating a one-way hash. The main operating systems we are covering here -- NT, Netware, and Unix -- all use an algorithm that has been made publically available and has been scrutinized to some degree.
To crack a password requires getting a copy of the one-way hash stored on the server, and then using the algorithm generate your own hash until you get a match. When you get a match, whatever word you used to generate your hash will allow you to log into that system. Since this can be rather time-consuming, automation is typically used. There are freeware password crackers available for NT, Netware, and Unix.
2. Why protect the hashes?
If the one-way hashes are not the password itself but a mathematical derivative, why should they be protected? Well, since the algorithm is already known, a password cracker could be used to simply encrypt the possible passwords and compare the one-way hashes until you get a match. There are two types of approaches to this -- dictionary and brute force.
Usually the hashes are stored in a part of the system that has extra security to limit access from potential crackers.
3. What is a dictionary password cracker?
A dictionary password cracker simply takes a list of dictionary words, and one at a time encrypts them to see if they encrypt to the one way hash from the system. If the hashes are equal, the password is considered cracked, and the word tried from the dictionary list is the password.
Some of these dictionary crackers can "manipulate" each word in the wordlist by using filters. These rules/filters allow you to change "idiot" to "1d10t" and other advanced variations to get the most from a word list. The best known of these mutation filters are the rules that come with Crack (for Unix). These filtering rules are so popular they have been ported over to cracking software for NT.
If your dictionary cracker does not have manipulation rules, you can "pre-treat" the wordlist. There are plenty of wordlist manipulation tools that allow all kinds of ways to filter, expand, and alter wordlists. With a little careful planning, you can turn a small collection of wordlists into a very large and thorough list for dictionary crackers without those fancy word manipulations built in.
4. What is a brute force password cracker?
A brute force cracker simply tries all possible passwords until it gets the password. From a cracker perspective, this is usually very time consuming. However, given enough time and CPU power, the password eventually gets cracked.
Most modern brute force crackers allow a number of options to be specified, such as maximum password length or characters to brute force with.
5. Which method is best for cracking?
It really depends on your goal, the cracking software you have, and the operating system you are trying to crack. Let's go through several scenarios.
If you remotely retrieved the password file through some system bug, your goal may be to simply get logged into that system. With the password file, you now have the user accounts and the hashes. A dictionary attack seems like the quickest method, as you may simply want access to the box. This is typical if you have a method of leveraging basic access to gain god status.
If you already have basic access and used this access to get the password file, maybe you have a particular account you wish to crack. While a couple of swipes with a dictionary cracker might help, brute force may be the way to go.
If your cracking software does both dictionary and brute force, and both are quite slow, you may just wish to kick off a brute force attack and then go about your day. By all means, we recommend a dictionary attack with a pre-treated wordlist first, followed up by brute force only on the accounts you really want the password to.
You should pre-treat your wordlists if the machine you are going to be cracking from bottlenecks more at the CPU than at the disk controller. For example, some slower computers with extremely fast drives make good candidates for large pre-treated wordlists, but if you have the CPU cycles to spare you might want to let the cracking program's manipulation filters do their thing.
A lot of serious hackers have a large wordlist in both regular and pre-treated form to accommodate either need.
6. What is a salt?
To increase the overhead in cracking passwords, some algorithms employ salts to add further complexity and difficulty to the cracking of passwords. These salts are typically 2 to 8 bytes in length, and algorithmically introduced to further obfuscate the one-way hash. Of the major operating systems covered here, only NT does not use a salt. The specifics for salts for both Unix and Netware systems are covered in their individual password sections.
Historically, the way cracking has been done is to take a potential password, encrypt it and produce the hash, and then compare the result to each account in the password file. By adding a salt, you force the cracker to have to read the salt in and encrypt the potential password with each salt present in the password file. This increases the amount of time to break all of the passwords, although it is certainly no guarantee that the passwords can't be cracked. Because of this most modern password crackers when dealing with salts do give the option of checking a specific account.
7. What are the dangers of cracking passwords?
The dangers are quite simple, and quite real. If you are caught with a password file you do not have legitimate access to, you are technically in possession of stolen property in the eyes of the law. For this reason, some hackers like to run the cracking on someone else's systems, thereby limiting their liability. I would only recommend doing this on a system you have a legitimate or well-established account on if you wish to keep a good eye on things, but perhaps have a way of running the cracking software under a different account than your own. This way, if the cracking is discovered (as it often is -- cracking is fairly CPU-intensive), it looks to belong to someone else. Obviously, you would want to run this under system adminstrator priviledges as you may have a bit more control, such as assigning lower priority to the cracking software, and hiding the results (making it less obvious to the real administrator).
Being on a system you have legit access to also allows you better access to check on the progress. Of course, if it is known you are a hacker, you'll still be the first to be blamed whether the cracking software is yours or not!
Running the cracking software in the privacy of your own home has the advantage of allowing you to throw any and all computing power you have at your disposal at a password, but if caught (say you get raided) then there is little doubt whose cracking job is running. However, there are a couple of things you can do to protect yourself: encrypt your files. Only decrypt them when you are viewing them, and wipe and/or encrypt them back after you are done viewing them.
8. Is there any way I can open a password-protected Microsoft Office document?
Certainly! There are plenty of commercial programs that will do this, but we give props to Elcomsoft for fighting the DMCA. 30-day trial versions are available here
Password Hacking
BlazingTools Perfect Keylogger Lite (Keylogger)
BlazingTools Perfect Keylogger Lite:
Description:
Do you want to know what your buddy or colleague is typing? May be you want to control your family members - what are they doing on your computer? Some applications of the keylogger: - Monitor children's activity for parents - Monitor what programs opened and when - Recall what you wrote some time ago - Special purposes Features: - Invisible in Task Manager List - Logging texts typed in every application (including passwords and other hidden texts) - Log file is encrypted and can be protected with a password - Easy log viewing and management - Export log to HTML format - Possibility to specify target applications - Supports all Windows versions, including Windows XP - Very easy to use - Free version.
Download
Keyboard Spectator Free (Keylogger)
Keyboard Spectator Free
Description:
Keyboard Spectator is a multifunctional keyboard tracking software (a.k.a. key logger) that is widely used by both regular users and IT security specialists. The reason for such popularity is that this program does not just record keystrokes; it is capable of recording language specific characters (ex. umlauts), date and time certain window was initiated as well as the caption of that window. Thus, this software combines two very important qualities - it records all typed data, so that you won't lose it when your computer unexpectedly crashes, and it keeps the record of all keyboard activity. It allows you to monitor your children's activity at home or to make sure your employees do not use company's computers inappropriately.
Download
Ardamax Keylogger Lite (Keylogger)
Ardamax Keylogger Lite
Description
Ardamax Keylogger Lite is a small, freeware keylogger that captures users activity and saves it to a logfile. The logfile can be viewed as a text or web page. Use this tool to find out what is happening on your computer while your away, maintain a backup of your typed data automatically or use it to monitor your kids.
Download
Quick Keylogger (Keylogger)
Quick Keylogger
Description
WideStep Software presents light and affordable monitoring utility Quick Keylogger that supports 64 bit Windows as well as other OS. Simple download and deployment guarantees a smooth start of your work with the optimal set of features: keystrokes, websites and other monitoring options. Simple but clear HTML reports make Quick Keylogger a great solution for everyone. Quick Keylogger will save keystrokes by application, date and time, it will capture absolutely all keystrokes, all buttons pressed in your system. Unfortunately unlike Elite Keylogger it is not that invisible to anti-keyloggers and anti-viruses. Designed for Windows 9x, Windows XP and Windows Vista Quick Keylogger offers you stability and simplicity with the most usable number of features. Quick Keylogger works seemlessly in the background and you are the only one who knows the password to view the logs. Quick Keylogger is equipped with a calendar that lets you sort and review logs by specific dates and time. All recorded sessions are combined by user, date, month, and time. Quick Keylogger is easy-to-use, very simple and small (instant free download) tool, which you can carry on a floppy disk drive for your mobility and fast response.
Download
Hack BSNL Broadband For Speed
If you are a BSNL broadband user, chances are that you are facing DNS issues for the last few weeks or so. Their DNS servers are just unresponsive. The lookup takes a long duration and many times just time out. The solution? Use third party DNS servers or run your own one like djbdns. The easiest options is to use OpenDNS. Just reconfigure your network to use the following DNS servers:
208.67.222.222
208.67.220.220
Detailed instructions specific to your router are available in the OpenDNS website itself. After I reconfigured my Linksys router to use the above 2 IP addresses, my DNS problems just vanished! Other ‘freebies’ that come with OpenDNS are phishing filters and automatic URL correction. Even if your service provider’s DNS servers are working fine, you can still use OpenDNS just for these two special features.
Bypassing Vista SP1 Windows Genuine Advantage
The fact that Microsoft has relaxed its antipiracy mechanism built into Windows Vista concomitantly with the release of Service Pack 1 failed to stop hackers from providing a crack for the latest version of Windows Genuine Advantage Validation.
Various reports point out that Genuine Advantage Validation and Notifications versions 1.7.69.1 (1.7.0069.1) and 1.7.69.2 released in March 2008, following the March 18 availability of Windows Vista SP1 through Windows Update and the Microsoft Download Center, have been cracked.
The workaround is designed to be integrated with pirated copies of Windows XP and Windows Vista in order to render useless the WGA Validation mechanism. According to the reports, applying the WGA crack will permit users of counterfeit versions of Windows to access and download items from Windows Update, Microsoft Download Center and Microsoft Update. The pirated operating systems with the cracked WGA will pass all validations on Microsoft's websites and offer anything from updates to applications that are restricted to users of genuine operating systems only.
With the release of Windows Vista SP1, Microsoft has scrapped the Reduced Functionality Mode kill switch in its latest operating system. Users of pirated Vista, just as those of XP and Windows Server 2008 will only be informed of the fact that their operating system is no longer genuine. However, pirated versions of Windows are automatically blocked from downloading certain free applications as well as all updates except those labeled Critical. The WGA crack is designed to fix that.
"After the activation grace period has been exceeded the next logon will present the user with a message that directs the customer to activate that copy of Windows. That dialog includes a fifteen second delay before it can be dismissed. If they want to skip activation at that time they can wait for the fifteen seconds and choose "Activate Later" .
But the new story is different.That is Vista SP1 has been cracked successfully and it's possible to bypass the Windows Genuine Advantage to fool the OS to beleive it as genuine.The release of Service Pack 1 for Vista seems to put no combat against piracy.This crack is available for download on this site.
MORE INFORMATION ON THE CRACK(ACTIVATOR)
VistaSP1_1-Click Activator
Unlike the other cracks eg: Vista Loader 3.0.0.1(which has some known issues with dual booting systems) this crack has been designed to work on dual booting systems.
This crack has incorporated an automated installation process which makes it easy to install.You can select from 4 OEM Logos and licenses during installation and within a few seconds your copy will be activated.You can see the system activated upon restart.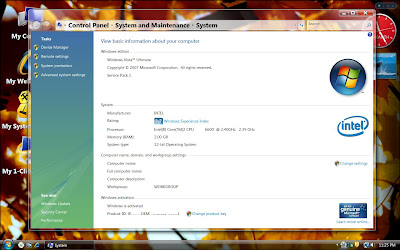
This crack also features the uninstallation process which most of the cracks lack the same.Using this is not necessary to carry out the manual uninstallation process.You can just uninstall the crack with a single click.
PLEASE FOLLOW THESE INSTRUCTIONS BEFORE APPLYING THIS CRACK.
1.YOU MUST HAVE FULL ADMINISTRATOR RIGHTS TO INSTALL THIS CRACK.
2.TURN OFF USER ACCOUNT CONTROL(UAC) BEFORE INSTALLING THIS CRACK.
3.THIS CRACK CURRENTLY WORKS ONLY WITH 32-BIT ULTIMATE EDITION OF WINDOWS VISTA.
4.EASY ONE CLICK ACTIVATOR.
5.YOU CAN ALSO USE THIS CRACK TO UNINSTALL THE ACTIVATOR.
ENJOY!!!
Here is the download link for the crack
DOWNLOAD
Please post your feedback through comments.
A File Embedder Project In C
Some times it is necessary for our compiled project to have it's supporting files embedded within the EXE module itself so that the supporting files may not be put into a seperate folder and carried along with the project.So here i am presenting you with the source code of the FILE EMBEDDER UTILITY project.
This utility can be used to embed one file with in the other.ie:Suppose we need to embed a .bat file(or any other file *.exe,*bmp,.txt.....) into our final project so that the batch file is present with in the compiled module and is hidden from the users avoiding tthe need to carry the .bat file every time with the project.
Both the Embedding and extraction process has been presented in seperate functions for your convenience.here's the code.....
#include<stdio.h>
#include<conio.h>
#include<fcntl.h>
#include<sys/types.h>
#include<sys/stat.h>
#include<stdlib.h>
#include<string.h>
void embed(void);
void extract(void);
char buff[1],sname[128],tname[128],dname[128],choice;
unsigned long int size=0;long int psize=0;int outh,bytes=0;
FILE *source,*target,*data;
void main()
{
while(1)
{
clrscr();
puts("\n\n\t\t\tFILE EMBEDDING UTILITY BY SRIKANTH\n\n\n");
puts("1.Embed A File 2. Extract A File 3.Exit\n");
choice=getch();
switch(choice)
{
case '1':embed();
getch();
break;
case '2':
extract();
getch();
break;
default:
exit(0);
}
}
}
void embed()
{
puts("\nEnter The Source Filename\n");
scanf("%s",sname);
source=fopen(sname,"rb+");
if(source==NULL)
{
puts("\nCannot Open The Source File\n");
return;
}
puts("\nEnter The Target Filename\n");
scanf("%s",tname);
outh=open(tname,O_RDONLYO_BINARY);
if(outh==-1)
{
puts("\nCannot Open The Target File\n");
return;
}
printf("\nReading The Source File Please Wait...\n");
while((bytes=read(outh,buff,1))>0)
size+=bytes;
data=fopen("Data.cfg","w");
if(data==NULL)
{
puts("\nCannot Create Configuration The File\n");
return;
}
fprintf(data,"%lu",size);
close(outh);
fclose(data);
target=fopen(tname,"rb");
if(target==NULL)
{
puts("Cannot Open Target File\n");
return;
}
printf("\nEmbedding Please Wait...\n");
fseek(source,0,SEEK_END);
while(fread(buff,1,1,target)>0)
fwrite(buff,1,1,source);
fcloseall();
printf("\nEmbedding Completed Successfully\n");
}
void extract()
{
printf("\nEnter The Source Filename\n");
scanf("%s",sname);
source=fopen(sname,"rb");
if(source==NULL)
{
printf("\nCannot Open The Source File\n");
return;
}
printf("\nEnter The Target Filename(eg: abc.exe)\n");
scanf("%s",tname);
printf("\nEnter The Configuration Filename(eg: DATA.cfg)\n");
scanf("%s",dname);
data=fopen(dname,"r");
if(data==NULL)
{
printf("\nConfiguration File Not Found\n");
return;
}
fscanf(data,"%ld",&psize);
target=fopen(tname,"wb");
if(target==NULL)
{
puts("\nCannot Open The Target File\n");
return;
}
printf("\nExtracting Please Wait...\n");
fseek(source,-psize,SEEK_END);
while((fread(buff,1,1,source))>0)
fwrite(buff,1,1,target);
printf("\nFile Extraction Completed Successfully\n");
fcloseall();
}
YOU CAN DOWNLOAD THE COMPILED MODULE OF THE ABOVE CODE HERE
Please pass your feedback through comments...........
Program To Hack Yahoo Accounts
There are number of sites which provide information about hacking email accounts.So what's special about this site? The only special about this site is that we do not bluff and mislead readers.We actually teach you how to track someone's email password rather than telling some nosense tricks to hack or crack someone's email.
One thing i'll make clear.There is no program that is particularly meant for hacking some one's email password.But it is still possible to sniff the password of the victim using some tools called Keyloggers OR Remote administration tools.For more information on Keyloggers refer this page.
I'll not elaborate this post since i have already discussed about- How to hack an email account.So this post is an addon to my previous post.Here i am giving information on two new programs that can be used to hack some one's email password or any other information "REMOTELY".You need not have physical accress to the victims PC.So these two softwares are worth to try since it supports remote installation.The following are the two new programs...
1.Remote Logger
Remote Logger Features:
Remote Installation - lets you to create a customized Remote Logger engine file. You can send this file to your target for remote monitoring.
Stealth mode
Very small size - Remote Logger is the smallest keylogger available!
Invisible mode - Remote Logger is invisible in the task bar, system tray, Windows 98/2000/XP/2003/Vista Task Manager, Start Menu and Windows Startup list.
Password capture - Remote Logger invisibly captures and records all passwords.
Email log delivery - log files can be invisibly emailed to you.
FTP Delivery - Remote Logger can upload recorded logs on the FTP server.
Keystroke logging and application monitoring - keylogger will record all keystrokes typed and all applications launched!
Unicode engine supports virtually all input languages, including Chinese, Japanese, Thai etc. Most competitive keyloggers record english keystrokes only.
Website logging - supports all popular browsers
Chat logging - supports all popular instant messengers
Screenshot recording
Powerful Log Viewer - offers an easy navigation through the log files.
Multi user support - Remote Logger can monitor all users of the PC.
Windows 98/NT/2000/XP/2003/Vista support
Friendly and easy to use user interface - even for novices!
2.SuperKeylogger
Superkeylogger features :
This program allows you to remotely install the monitoring system through an email attachment (no physical installation needed) without the user recognizing theinstallation at all.
User can set number of days in remote installation package after which Superkeylogger will uninstall itself automatically. (New)
User definable Server Name for remote installation package. (New)
No SMTP server required to send log mails.
Records applications activity showing you which programs were launched.
Records absolutely all keystrokes, including system keys.
Records all passwords, including passwords to e-mails and websites, etc.
Log both side Chat (Yahoo Messenger / Msn Messenger). (New)
Monitors Internet activity, websites and web-pages visited.
Captures all e-mails sent on monitored PC, no matter if it is Outlook or any other e-mail client, or the mail is sent using web-interface.
Records desktop activity by taking snapshots of your desktop at a customizable interval.
Unique un-hiding mechanism - you can choose any secret word to unhide the Super key logger.
Simple installation/un-installation - suitable for all users
Automatically & Invisibly send logs to predefined email address on customizable intervals.
Automatically & invisibly send logs to any predefined FTP address. (New)
Automatically removal of already emailed log files.
Extremely low system requirements.
Absolutely invisible.
Each entry in the log is accompanied by detailed information (time, date, username, application, etc)
Monitors all users on your PC.
Easily configurable.
Automatic startup with system startup.
Thse two softwares are none other than keyloggers but supports remote installation..
Disable Task Manager
WARNING: Please Backup your registry before attemting this hack.Changes to registry may lead to system failure.
The following registry hack enables us to disable the Task Manager.
Step1: Goto start>run and type "regedit" in the run.
Step2: In the registry navigate to
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System
Value Name: DisableTaskMgr
Data Type: REG_DWORD (DWORD Value)
Value Data: (0 = default, 1 = disable Task Manager)
Step 3: Then navigate to
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System
Value Name: DisableTaskMgr
Data Type: REG_DWORD (DWORD Value)
Value Data: (0 = default, 1 = disable Task Manager)
Advanced Google Search
Google is clearly the best general-purpose search engine on the Web.But most people don't use it to its best advantage. Do you just plug in a keyword or two and hope for the best? That may be the quickest way to search, but with more than 3 billion pages in Google's index, it's still a struggle to pare results to a manageable number.
But Google is an remarkably powerful tool that can ease and enhance your Internet exploration. Google's search options go beyond simple keywords, the Web, and even its own programmers. Let's look at some of Google's lesser-known options.
Syntax Search Tricks
Using a special syntax is a way to tell Google that you want to restrict your searches to certain elements or characteristics of Web pages.Here are some advanced operators that can help narrow down your search results.
1.Intitle: at the beginning of a query word or phrase (intitle:"Three Blind Mice") restricts your search results to just the titles of Web pages.
2.Intext: does the opposite of intitle:, searching only the body text, ignoring titles, links, and so forth. Intext: is perfect when what you're searching for might commonly appear in URLs. If you're looking for the term HTML, for example, and you don't want to get results such as
www.gohacking.com/index.html
you can enter intext:html
3.Link: lets you see which pages are linking to your Web page or to another page you're interested in. For example, try typing in
link:http://www.gohacking.com/
3.site: (which restricts results to top-level domains) with intitle: to find certain types of pages. For example, get scholarly pages about Mark Twain by searching for intitle:"Mark Twain"site:edu. Experiment with mixing various elements; you'll develop several strategies for finding the stuff you want more effectively. The site: command is very helpful as an alternative to the mediocre search engines built into many sites.
Swiss Army Google
Google has a number of services that can help you accomplish tasks you may never have thought to use Google for. For example, the new calculator feature
(www.google.com/help/features.html#calculator)
lets you do both math and a variety of conversions from the search box. For extra fun, try the query "Answer to life the universe and everything."
Suppose you want to contact someone and don't have his phone number handy. Google can help you with that, too. Just enter a name, city, and state. (The city is optional, but you must enter a state.) If a phone number matches the listing, you'll see it at the top of the search results along with a map link to the address. If you'd rather restrict your results, use rphonebook: for residential listings or bphonebook: for business listings. If you'd rather use a search form for business phone listings, try Yellow Search
(www.buzztoolbox.com/google/yellowsearch.shtml).
Let Google help you figure out whether you've got the right spelling—and the right word—for your search. Enter a misspelled word or phrase into the query box (try "thre blund mise") and Google may suggest a proper spelling. This doesn't always succeed; it works best when the word you're searching for can be found in a dictionary. Once you search for a properly spelled word, look at the results page, which repeats your query. (If you're searching for "three blind mice," underneath the search window will appear a statement such as Searched the web for "three blind mice.") You'll discover that you can click on each word in your search phrase and get a definition from a dictionary.
Extended Googling
Google offers several services that give you a head start in focusing your search. Google Groups
(http://groups.google.com/)
indexes literally millions of messages from decades of discussion on Usenet. Google even helps you with your shopping via two tools: FroogleCODE(http://froogle.google.com/),
which indexes products from online stores, and Google CatalogsCODE(http://catalogs.google.com/),
which features products from more 6,000 paper catalogs in a searchable index. And this only scratches the surface. You can get a complete list of Google's tools and services at
www.google.com/options/index.html
You're probably used to using Google in your browser. But have you ever thought of using Google outside your browser?
Google Alert
(http://www.googlealert.com/)
monitors your search terms and e-mails you information about new additions to Google's Web index. (Google Alert is not affiliated with Google; it uses Google's Web services API to perform its searches.) If you're more interested in news stories than general Web content, check out the beta version of Google News Alerts
(www.google.com/newsalerts).
This service (which is affiliated with Google) will monitor up to 50 news queries per e-mail address and send you information about news stories that match your query. (Hint: Use the intitle: and source: syntax elements with Google News to limit the number of alerts you get.)
Google on the telephone? Yup. This service is brought to you by the folks at Google Labs
(http://labs.google.com/),
a place for experimental Google ideas and features (which may come and go, so what's there at this writing might not be there when you decide to check it out). With Google Voice Search
(http://labs1.google.com/gvs.html),
you dial the Voice Search phone number, speak your keywords, and then click on the indicated link. Every time you say a new search term, the results page will refresh with your new query (you must have JavaScript enabled for this to work). Remember, this service is still in an experimental phase, so don't expect 100 percent success.
In 2002, Google released the Google API (application programming interface), a way for programmers to access Google's search engine results without violating the Google Terms of Service. A lot of people have created useful (and occasionally not-so-useful but interesting) applications not available from Google itself, such as Google Alert. For many applications, you'll need an API key, which is available free fromCODEwww.google.com/apis
SOURCE:http://www.pcmag.com/
Hacking Hotmail Password
These are some of the tricks that you can try to hack hotmail passwords.
Brute force hacking
a. Use telnet to connect to port 110 (Hotmail´s pop-server)
b. Type USER and then the victim´s username
c. Type PASS and then the guess a password
d. Repeat that until U have found the correct password.
!. This is called brute force hacking and requires patience.
It´s better than trying to guess the victims password on
hotmail homepage only because it´s faster.
The Best way
a. Get the username of the victim (It usually stands in the adress-field )
b. Then type " www.hotmail.com/cgi-bin/start/victimsusername "
c. U´re in!
!. This hack only work if U are on the same network or computer as the
victim and if he don´t log out.
The old way
a. Go to http://www.hotmail/proxy.html
b. Now type the victims username. (press login)
c. Look at the source code.
d. On the fifth row U should find "action=someadress"
e. Copy that adress and paste it into the adress-field
f. You are in...
!. As you can see it´s a long procedure and the victim have
plenty of time to log out.
Another...
a. Go to hotmail´s homepage
b. Copy the source code.
c. Make a new html file with the same code but change method=post to
method=enter
d. "view" the page
e. Change the adress to www.hotmail.com/ (don´t press enter!)
f. Make the victim type in his username and password
g. Look in the adress-field. There you´ll see ...&password:something...
!. This is the way I use, because it lets you know the password.
(If he exits the browser U can see the password in the History folder!)
MUST READ!
Hotmail´s system operators have changed the "system" so that the victim may logout even if U are inside his/her account. So don´t waste U´r time!
So you want to get some hotmail passwords?
This is pretty easy to do once you have got the hang of it. If you are a beginner, I wouldn't make this your first attempt at hacking. When you need to do is use a port surfer and surf over to port 80. While there, you have to try and mail the user that you want the password from.
It is best to mail them using the words
"We" and "Here at Hotmail..."
Most suckers fall for this and end up giving out their password. There is another way to also, you can get an anon mailer, and forge the addres as staff@hotmail.com. But you have to change the reply address to go to a different addres like user@host.com. The person that you are trying to get the pass from MUST respond to that letter for the mail to be forwarded to you. Have text like "Please reply to this letter with the subject "PASSWORD" and underneith please include your user name and password.
If you have trouble Loging in withing the next few days, this is only because we are updating our mail servers but no need to worry, your mail will still be there. Even though the server may be down for an hour. From the staff at Hotmail, Thank You."
For a detailed information on how to send fake emails click here
Change The Title Of Yahoo Messenger
Here’s how you change the title text that appears at the top of the Messenger window. By default, this is “Yahoo! Messenger”, followed by your status. Simply edit the ymsgr.ini file, which you will find in the same folder as the Messenger program, in your Program Files folder. Locate the file and open it in Notepad. Then, at the end, add the following:
[APP TITLE]
caption=YOUR TEXT
Here, “YOUR TEXT” is whatever you want in the title bar. Save the file and close Messenger. When you restart it you will see your text in the title bar.
Email Tracking
One of most the frequently asked question is how to track an email back to the sender.That is how to determine the sender of the email? The most obvious answer is by looking at the "From:" line! But this does not work all the time since most of the spammers forge the email address or most of the spam that we get has a forged email address.This is also known as a spoofed email.Is it possible to send email from other's address?Yes it is possible to send email from anyone's name.Why not, you can send an email even from Bill Gate's Email ID.If you need a proof look here!
For more information on how to send a spoofed email refer this post.
OK now let's come back to the topic of email tracking.So how do you determine where a message actually came from?For that you have to understand how email messages are put together in order to backtrack an email message. SMTP is a text based protocol for transferring messages across the internet. A series of headers are placed in front of the data portion of the message. By examining the headers you can usually backtrack a message to the source network, sometimes the source host. A more detailed essay on reading email headers can be found .
If you are using Outlook or Outlook Express you can view the headers by right clicking on the message and selecting properties or options.
Below are listed the headers of an actual spam message.I have double spaced the headers to make them more readable.
Return-Path: <s359dyxtt@yahoo.com>
X-Original-To: sriki@example.com
Delivered-To: sriki@example.com
Received: from 12-218-172-108.client.mchsi.com (12-218-172-108.client.mchsi.com [12.218.172.108])by mailhost.example.com (Postfix) with SMTP id 1F9B8511C7for <sriki@example.com>; Sun, 16 Nov 2003 09:50:37 -0800 (PST)
Received: from (HELO 0udjou) [193.12.169.0] by 12-218-172-108.client.mchsi.com with ESMTP id <536806-74276>; Sun, 16 Nov 2003 19:42:31 +0200
Message-ID: <n5-l067n7z$46-z$-n@eo2.32574>
From: "Maricela Paulson" <s359dyxtt@yahoo.com>
Reply-To: "Maricela Paulson" <s359dyxtt@yahoo.com>
To: sriki@example.com
Subject: You Have won $10000 in US Lottery Scheme
Date: Sun, 16 Nov 2003 19:42:31 +0200
X-Mailer: Internet Mail Service (5.5.2650.21)
X-Priority: 3
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary="MIMEStream=_0+211404_90873633350646_4032088448"
According to the From header this message is from Maricela Paulson at s359dyxxt@yahoo.com. I could just fire off a message to abuse@yahoo.com, but that would be waste of time. This message didn't come from yahoo's email service.
The header most likely to be useful in determining the actual source of an email message is the Received header. According to the top-most Received header this message was received from the host 12-218-172-108.client.mchsi.com with the ip address of 21.218.172.108 by my server mailhost.example.com. An important item to consider is at what point in the chain does the email system become untrusted? I consider anything beyond my own email server to be an unreliable source of information. Because this header was generated by my email server it is reasonable for me to accept it at face value.
The next Received header (which is chronologically the first) shows the remote email server accepting the message from the host 0udjou with the ip 193.12.169.0. Those of you who know anything about IP will realize that that is not a valid host IP address. In addition, any hostname that ends in client.mchsi.com is unlikely to be an authorized email server. This has every sign of being a cracked client system.
Here's is where we start digging. By default Windows is somewhat lacking in network diagnostic tools; however, you can use the tools at to do your own checking.
sriki@nqh9k:[/home/sriki] $whois 12.218.172.108 AT&T WorldNet Services ATT (NET-12-0-0-0-1)12.0.0.0 - 12.255.255.255Mediacom Communications Corp MEDIACOMCC-12-218-168-0-FLANDREAU-MN (NET-12-218-168-0-1)12.218.168.0 - 12.218.175.255
# ARIN WHOIS database, last updated 2003-12-31 19:15# Enter ? for additional hints on searching ARIN's WHOIS database.
I can also verify the hostname of the remote server by using nslookup, although in this particular instance, my email server has already provided both the IP address and the hostname.
sriki@nqh9k:[/home/sriki] $nslookup 12.218.172.108
Server: localhostAddress: 127.0.0.1
Name: 12-218-172-108.client.mchsi.comAddress: 12.218.172.108
Ok, whois shows that Mediacom Communications owns that netblock and nslookup confirms the address to hostname mapping of the remote server,12-218-172-108.client.mchsi.com. If I preface a www in front of the domain name portion and plug that into my web browser, http://www.mchsi.com/, I get Mediacom's web site.
There are few things more embarrassing to me than firing off an angry message to someone who is supposedly responsible for a problem, and being wrong. By double checking who owns the remote host's IP address using two different tools (whois and nslookup) I minimize the chance of making myself look like an idiot.
A quick glance at the web site and it appears they are an ISP. Now if I copy the entire message including the headers into a new email message and send it to abuse@mchsi.com with a short message explaining the situation, they may do something about it.
But what about Maricela Paulson? There really is no way to determine who sent a message, the best you can hope for is to find out what host sent it. Even in the case of a PGP signed messages there is no guarantee that one particular person actually pressed the send button. Obviously determining who the actual sender of an email message is much more involved than reading the From header. Hopefully this example may be of some use to other forum regulars.
Change IP Address
How to change your IP address in less than a minute? The following trick gives you a step-by-step procedure to change your IP address.
1. Click on "Start" in the bottom left hand corner of screen.
2. Click on "Run".
3. Type in "command" and hit ok.You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter".
5. Type "exit" and leave the prompt.
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties".
You should now be on a screen with something titled "Local Area Connection", or something close to that.
8. Right click on "Local Area Connection" and click "properties".
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab.
10. Click on "Use the following IP address" under the "General" tab.
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here.
14. Hit the "Ok" button again.You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings.
17. This time, select "Obtain an IP address automatically".
18. Hit "Ok".
19. Hit "Ok" again.
20. You now have a new IP address.
Some ISPs do not support this type of procedure and hence there are chances of getting back the same old IP address even after trying this hack.In this case you need to switch off the modem and then switch it on to get the new IP address.
NOTE: All these tricks works only if you have a dynamic IP address.But if you have a static IP address you have no option to change your IP.
How To Disable Windows Logo Key?
At times it becomes necessary to disable the Windows Key on the keyboard.For example when playing games this nasty Windows Logo key keeps annoying , as we often accidently press it and this takes our game out to the desktop.So it becomes necessary to disable it when not needed an re-enable it when needed.
The following download consists of two registry scripts (.reg) one to disable windows key and the other to re-enable it.In this download there are two files
disable_winlogo_key.reg - Disable Windows Logo Ley
re-enable_winlogo_key.reg - Re-Enable Windows Logo Key
DOWNLOAD










