Description
VMware and experts alike are urging users to patch multiple products affected by a critical authentication bypass vulnerability that can allow an attacker to gain administrative access to a system as well as exploit other flaws.
The bug—tracked as CVE-2022-31656—earned a rating of 9.8 on the CVSS and is one of a number of fixes the company made in various products in an update released on Tuesday for flaws that could easily become an exploit chain, researchers said.
CVE-2022-31656 also certainly the most dangerous of these vulnerabilities, and likely will become more so as the researcher who discovered it–Petrus Viet of VNG Security–has promised in a tweet that a proof-of-concept exploit for the bug is “soon to follow,” experts said.
This adds urgency to the need for organizations affected by the flaw to patch now, researchers said.
“Given the prevalence of attacks targeting VMware vulnerabilities and a forthcoming proof-of-concept, organizations need to make patching CVE-2022-31656 a priority,” Claire Tills, senior research engineer with Tenable’s Security Response Team, said in an email to Threatpost. “As an authentication bypass, exploitation of this flaw opens up the possibility that attackers could create very troubling exploit chains.”
Potential for Attack Chain
Specifically, CVE-2022-31656 is an authentication bypass vulnerability affecting VMware Workspace ONE Access, Identity Manager and vRealize Automation.
The bug affects local domain users and requires that a remote attacker must have network access to a vulnerable user interface, according to a blog post by Tills published Tuesday. Once an attacker achieves this, he or she can use the flaw to bypass authentication and gain administrative access, she said.
Moreover, the vulnerability is the gateway to exploiting other remote code execution (RCE) flaws addressed by VMWare’s release this week—CVE-2022-31658 and CVE-2022-31659—to form an attack chain, Tills observed.
CVE-2022-31658 is a JDBC injection RCE vulnerability that affect VMware Workspace ONE Access, Identity Manager and vRealize Automation that’s earned an “important” score on the CVSS—8.0. The flaw allows a malicious actor with administrator and network access to trigger RCE.
CVE-2022-31659 is an SQL injection RCE vulnerability that affects VMware Workspace ONE Access and Identity Manager and also earned a rating of 8.0 with a similar attack vector to CVE-2022-31658. Viet is credited with discovering both of these flaws.
The other six bugs patched in the update include another RCE bug (CVE-2022-31665) rated as important; two privilege escalation vulnerabilities (CVE-2022-31660 and CVE-2022-31661) rated as important; a local privilege escalation vulnerability (CVE-2022-31664) rated as important; a URL Injection Vulnerability (CVE-2022-31657) rated as moderate; and a path traversal vulnerability (CVE-2022-31662) rated as moderate.
Patch Early, Patch Everything
VMware is no stranger to having to rush out patches for critical bugs found in its products, and has suffered its share of security woes due to the ubiquity of its platform across enterprise networks.
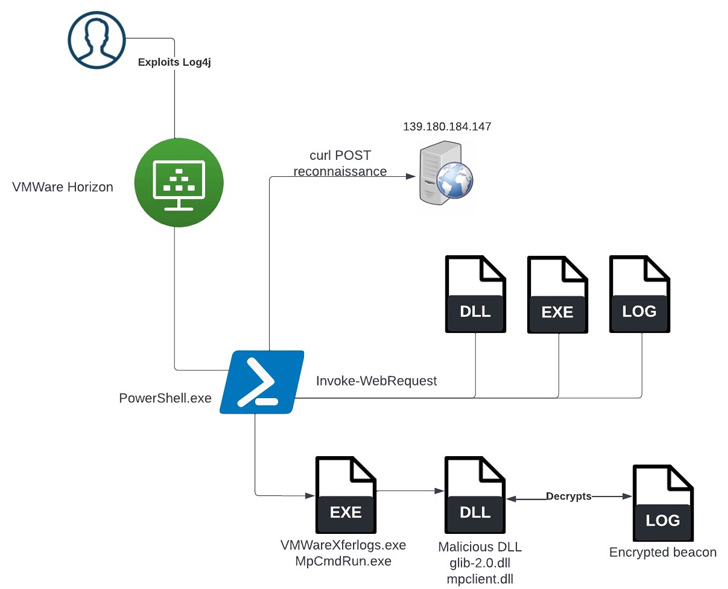
In late June, for example, federal agencies warned of attackers pummeling VMware Horizon and Unified Access Gateway (UAG) servers to exploit the now-infamous Log4Shell RCE vulnerability, an easy-to-exploit flaw discovered in the Apache logging library Log4J late last year and continuously targeted on VMware and other platforms since then.
Indeed, sometimes even patching has still not been enough for VMware, with attackers targeting existing flaws after the company does its due diligence to release a fix.
This scenario occurred in December 2020, when the feds warned the adversaries were actively exploiting a weeks-old bug in Workspace One Access and Identity Manager products three days after the vendor patched the vulnerability.
Though all signs point to the urgency of patching the latest threat to VMware’s platform, it’s highly likely that even if the advice is heeded, the danger will persist for the foreseeable future, observed one security professional.
Though enterprises tend to initially move quickly to patch the most imminent threats to their network, they often miss other places attackers can exploit a flaw, observed Greg Fitzgerald, co-founder of Sevco Security, in an email to Threatpost. This is what leads to persistent and ongoing attacks, he said.
“The most significant risk for enterprises isn’t the speed at which they are applying critical patches; it comes from not applying the patches on every asset,” Fitzgerald said. “The simple fact is that most organizations fail to maintain an up-to-date and accurate IT asset inventory, and the most fastidious approach to patch management cannot ensure that all enterprise assets are accounted for.”