As
2021 draws to a close, and the COVID-19 pandemic drags on, it’s time to
take stock of what resonated with our 1 million+ monthly visitors this
year, with an eye to summing up some hot trends (gleaned from looking at
the most-read stories on the Threatpost site).
While 2020 was all about work-from-home security, COVID-19-themed
social engineering and gaming (all driven by social changes during Year
One of the pandemic), 2021 saw a distinctive shift in interest. Data
insecurity, code-repository malware, major zero-day vulnerabilities and
fresh ransomware tactics dominated the most-read list – perhaps
indicating that people are keenly focused on cybercrime innovation as
the “new normal” for how we work becomes more settled in.
Jump to section:
- Data Leakapalooza
- Major Zero-Day Vulnerabilities
- Code Repository Malware
- Ransomware Innovations
- Gaming Attacks
- Bonus! Zodiac Killer Cipher Cracked
1. The Most-Read Story of 2021: Experian Leaks Everyone’s Credit Scores
There were obviously some huge news stories that dominated headlines
during the year: Log4Shell; Colonial Pipeline; Kaseya;
ProxyLogon/ProxyShell; SolarWinds. But judging from article traffic,
readers were most interested in…the Experian data exposure.
In April, Bill Demirkapi, a sophomore student at the Rochester
Institute of Technology, discovered that the credit scores of almost
every American were exposed
through an API tool used by the Experian credit bureau, which he said
was left open on a lender site without even basic security protections.
The tool, called the Experian Connect API, allows lenders to automate
FICO-score queries. Demirkapi said he was able to build a command-line
tool that let him automate lookups for any credit score for nearly
anyone, even after entering all zeros in the fields for date of birth,
which he named, “Bill’s Cool Credit Score Lookup Utility.”
In addition to raw credit scores, the college student said that he
was able to use the API connection to get “risk factors” from Experian
that explained potential flaws in a person’s credit history, such as
“too many consumer-finance company accounts.”
Experian, for its part, fixed the problem – and refuted concerns from the security community that the issue could be systemic.
Experian wasn’t the only household name that drew in readers for data
insecurity: LinkedIn data going up for sale on the Dark Web was another
very hot story this year.
LinkedIn Data Scraping
After 500 million LinkedIn members were affected in a data-scraping incident in April, it happened again
in June. A posting with 700 million LinkedIn records for sale appeared
on popular cyberattacker destination RaidForums, by a hacker calling
himself “GOD User TomLiner.” The advertisement included a sample of 1
million records as “proof.”
Privacy Sharks examined the free sample and saw that the records
include full names, gender, email addresses, phone numbers and industry
information. It’s unclear what the origin of the data is – but the
scraping of public profiles is a likely source. According to LinkedIn,
no breach of its networks occurred.
Even so, the security ramifications were significant, researchers
said, in terms of the cache enabling brute-force cracking of account
passwords, email and telephone scams, phishing attempts, identity theft
and finally, the data could be a social-engineering goldmine. Sure,
attackers could simply visit public profiles to target someone, but
having so many records in one place could make it possible to automate
targeted attacks using information about users’ jobs and gender, among
other details.
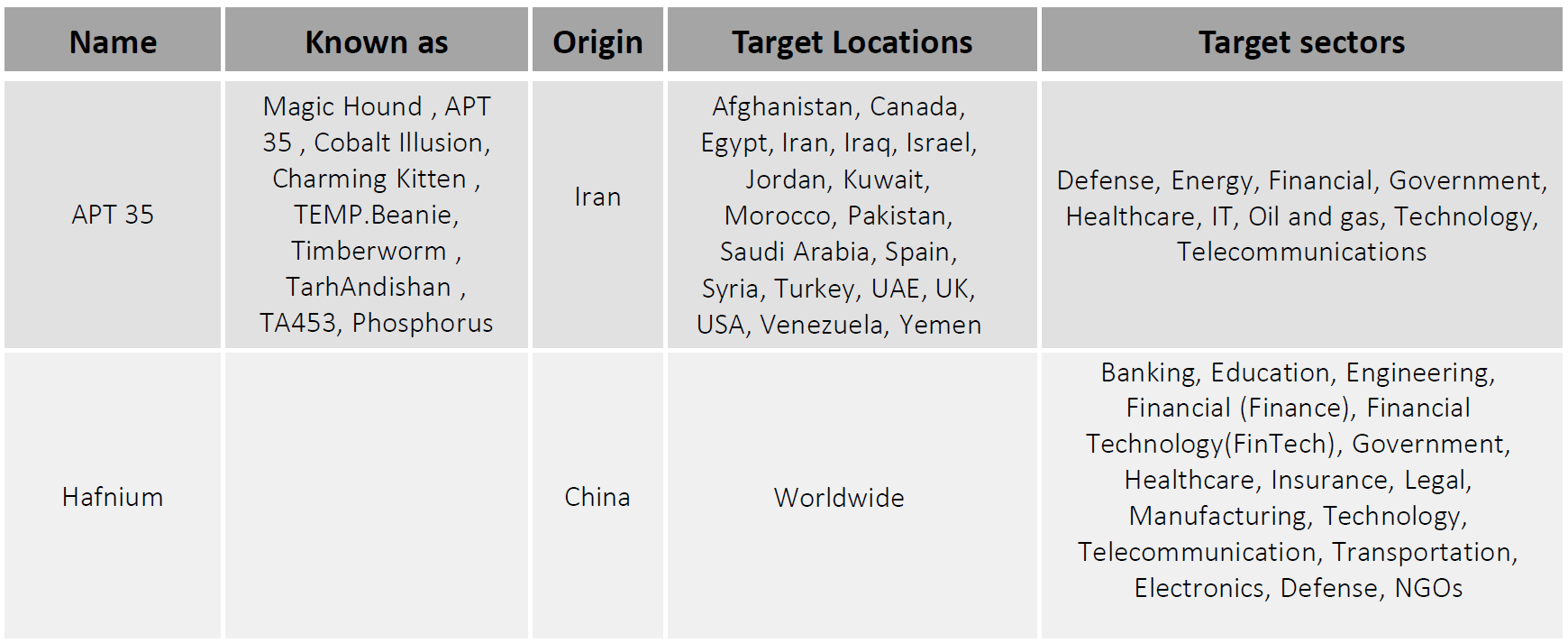
2. Major Zero-Day Bugs
OK, this one’s a perennial topic of fascination, but 2021 had some doozies, starting with Log4Shell.
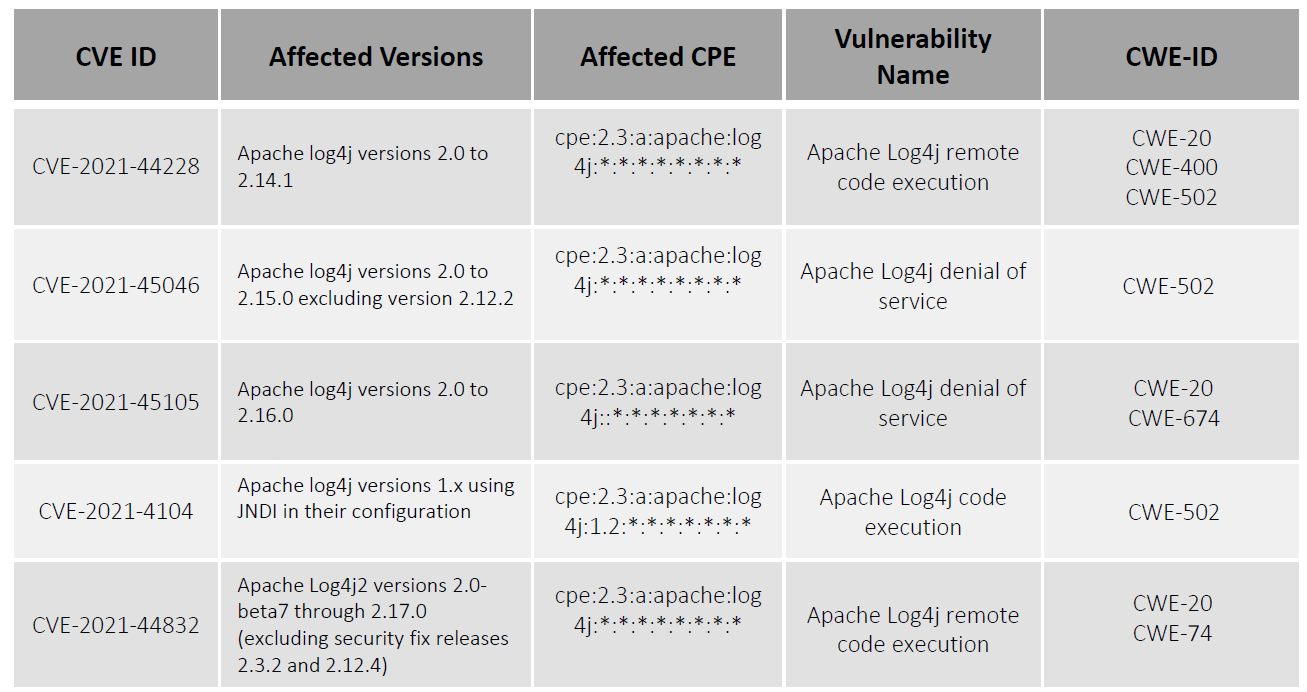
Log4Shell Threatens Basically All Web Servers in Existence
The Log4Shell vulnerability is an easily exploited flaw
in the ubiquitous Java logging library Apache Log4j could allow
unauthenticated remote code execution (RCE) and complete server takeover
— and it’s still being actively exploited in the wild.
The flaw (CVE-2021-44228) first turned up on sites that cater to
users of the world’s favorite game, Minecraft. Apache rushed a patch but
within a day or two, attacks became rampant as threat actors tried to
exploit the new bug. From there, news of additional exploitation
vectors, a second bug, various kinds of real-world attacks and the sheer
enormity of the threat surface (the logging library is basically
everywhere) dominated reader interest in December.
NSO Group’s Zero-Click Zero Day for Apple
In September, a zero-click zero-day
dubbed ForcedEntry be researchers was found, affecting all things
Apple: iPhones, iPads, Macs and Watches. It turns out that it was being
exploited by NSO Group to install the infamous Pegasus spyware.
Apple pushed out an emergency fix, but Citizen Lab had already
observed the NSO Group targeting never-before-seen, zero-click exploit
targeting iMessage to illegally spy on Bahraini activists.
The ForcedEntry exploit was particularly notable in that it was
successfully deployed against the latest iOS versions – 14.4 & 14.6 –
blowing past Apple’s new BlastDoor sandboxing feature to install
spyware on the iPhones of the Bahraini activists.
Giant Zero-Day Hole in Palo Alto Security Appliances
Another zero-day item that garnered big reader interest was the news
that researchers from Randori developed a working exploit to gain
remote code execution (RCE) on Palo Alto Networks’ GlobalProtect
firewall, via the critical bug CVE 2021-3064.
Randori researchers said that if an attacker successfully exploits
the weakness, they can gain a shell on the targeted system, access
sensitive configuration data, extract credentials and more. And after
that, attackers can dance across a targeted organization, they said:
“Once an attacker has control over the firewall, they will have
visibility into the internal network and can proceed to move laterally.”
Palo Alto Networks patched the bug on the day of disclosure.
The Great Google Memory Bug Zero-Day
In March, Google hurried out a fix
for a vulnerability in its Chrome browser that was under active attack.
If exploited, the flaw could allow remote code-execution and
denial-of-service attacks on affected systems. Readers flocked to the
coverage of the issue.

New york, USA – july 26, 2019: Start google chrome application on computer macro close up view in pixel screen
The flaw is a use-after-free vulnerability, and specifically exists
in Blink, the browser engine for Chrome developed as part of the
Chromium project. Browser engines convert HTML documents and other web
page resources into the visual representations viewable to end users.
“By persuading a victim to visit a specially crafted website, a
remote attacker could exploit this vulnerability to execute arbitrary
code or cause a denial-of-service condition on the system,” according to
IBM X-Force’s report on the bug.
Dell Kernel-Privilege Bugs
Earlier this year, five high-severity security bugs that remained hidden for 12 years were found
to exist in all Dell PCs, tablets and notebooks shipped since 2009.
They allow the ability to bypass security products, execute code and
pivot to other parts of the network for lateral movement, according to
SentinelLabs.
The flaws lurked in Dell’s firmware update driver, impacting
potentially hundreds of millions of Dell desktops, laptops, notebooks
and tablets, researchers said.
The multiple local privilege-escalation (LPE) bugs exist in the
firmware update driver version 2.3 (dbutil_2_3.sys) module, which has
been in use since 2009. The driver component handles Dell firmware
updates via the Dell BIOS Utility, and it comes pre-installed on most
Dell machines running Windows.
3. Code Repositories and the Software Supply Chain
The software supply chain is anchored by open-source code
repositories – centralized locations where developers can upload
software packages for use by developers in building various
applications, services and other projects. They include GitHub, as well
as more specialized repositories like the Node.js package manager (npm)
code repository for Java; RubyGems for the Ruby programming language;
Python Package Index (PyPI) for Python; and others.
These package managers represent a supply-chain threat given that
anyone can upload code to them, which can in turn be unwittingly used as
building blocks in various applications. Any applications corrupted by
malicious code can attack the programs’ users.
To boot, a single malicious package can be baked into multiple
different projects – infecting them with cryptominers, info-stealers and
more, and making remediation a complex process.
Cybercriminals have swarmed to this attack surface, and readers in 2021 loved to hear about their exploits.
For instance, in December, a series of 17 malicious packages
in npm were found; they were all built to target Discord, the virtual
meeting platform used by 350 million users that enables communication
via voice calls, video calls, text messaging and files. The coal was to
steal Discord tokens, which can be used to take over accounts.
Also this month, three malicious packages hosted in the PyPI code repository were uncovered,
which collectively have more than 12,000 downloads – and presumably
slithered into installations in various applications. The packages
included one trojan for establishing a backdoor on victims’ machines,
and two info-stealers.
Researchers also discovered last week that there were 17,000
unpatched Log4j Java packages in the Maven Central ecosystem, leaving
massive supply-chain risk on the table from Log4Shell exploits. It will likely take “years” for it to be fixed across the ecosystem, according to Google’s security team.
Using malicious packages as a cyberattack vector was a common theme
earlier in the year too. Here’s a rundown of other recent discoveries:
- In January, other Discord-stealing malware was discovered
in three npm packages. One, “an0n-chat-lib” had no legitimate “twin”
package, but the other two made use of brandjacking and typosquatting to
lure developers into thinking they’re legitimate. The “discord-fix”
malicious component is named to be similar to the legitimate
“discord-XP,” an XP framework for Discord bots. The “sonatype” package
meanwhile made use of pure brandjacking.
- In March, researchers spotted
malicious packages targeting internal applications for Amazon, Lyft,
Slack and Zillow (among others) inside the npm public code repository –
all of which exfiltrated sensitive information.
- That March attack was based on research from security researcher Alex Birsan, who found that it’s possible to inject malicious code
into common tools for installing dependencies in developer projects.
Such projects typically use public repositories from sites like GitHub.
The malicious code then can use these dependencies to propagate malware
through a targeted company’s internal applications and systems. The
novel supply-chain attack was (ethically) used to breached the systems
of more than 35 technology players, including Microsoft, Apple, PayPal,
Shopify, Netflix, Tesla and Uber, by exploiting public, open-source
developer tools.
- In June, a group of cryptominers was found to have infiltrated the PyPI. Researchers found six different malicious packages hiding there, which had a collective 5,000 downloads.
- In July, a credentials-stealing package that uses legitimate password-recovery tools in Google’s Chrome web browser was found lurking in npm.
Researchers caught the malware filching credentials from Chrome on
Windows systems. The password-stealer is multifunctional: It also
listens for incoming commands from the attacker’s command-and-control
(C2) server and can upload files, record from a victim’s screen and
camera, and execute shell commands.
4. Interesting Ransomware Variants
The ransomware epidemic matured in 2021, with the actual malware used
to lock up files progressing beyond simply slapping an extension on
targeted folders. Readers flocked to malware analysis stories covering
advancements in ransomware strains, including the following Top 3
discoveries.
HelloKitty’s Linux Variant Targets VMs
In June, for the first time, researchers publicly spotted a Linux encryptor – being used by the HelloKitty ransomware gang.
HelloKitty, the same group behind the February attack
on videogame developer CD Projekt Red, has developed numerous Linux
ELF-64 versions of its ransomware, which it used to target VMware ESXi
servers and virtual machines (VMs) running on them.
VMware ESXi, formerly known as ESX, is a bare-metal hypervisor that
installs easily onto servers and partitions them into multiple VMs.
While that makes it easy for multiple VMs to share the same hard-drive
storage, it sets systems up to be one-stop shopping spots for attacks,
since attackers can encrypt the centralized virtual hard drives used to
store data from across VMs.
Dirk Schrader of New Net Technologies (NNT) told Threatpost that on
top of the attraction of ESXi servers as a target, “going that extra
mile to add Linux as the origin of many virtualization platforms to
[malware’s] functionality” has the welcome side effect of enabling
attacks on any Linux machine.
MosesStaff: No Decryption Available
A politically motivated group known as MosesStaff was seen in November
paralyzing Israeli entities with no financial goal – and no intention
of handing over decryption keys. Instead, it was using ransomware in
politically motivated, destructive attacks at Israeli targets, looking
to inflict the most damage possible.
MosesStaff encrypts networks and steals information, with no
intention of demanding a ransom or rectifying the damage. The group also
maintains an active social-media presence, pushing provocative messages
and videos across its channels, and making its intentions known.
Epsilon Red Targets Exchange Servers
Threat actors in June were seen deploying new ransomware on the back of a set of PowerShell scripts developed for exploiting flaws in unpatched Exchange Servers.
The Epsilon Red ransomware – a reference to an obscure enemy
character in the X-Men Marvel comics, a super soldier of Russian origin
armed with four mechanical tentacles – was discovered after an attack on
a U.S.-based company in the hospitality sector.
Researchers said the ransomware was different in the way it spreads
its hooks into a corporate network. While the malware itself is a
“bare-bones” 64-bit Windows executable programmed in the Go programming
language, its delivery system relies on a series of PowerShell scripts
that “prepared the attacked machines for the final ransomware payload
and ultimately delivered and initiated it,” they wrote.
5. Gaming Security
For the second year in a row, gaming security was on the radar for
readers in 2021, possibly because cybercriminals continue to target this
area as result of the global COVID-19 pandemic driving higher volumes
of play. In a recent survey by Kaspersky, nearly 61 percent reported
suffering foul play such as ID theft, scams or the hack of in-game
valuables. Some of the most popular articles are recapped below.
Steam Used to Host Malware
In June, the appropriately named SteamHide malware emerged, which disguises itself inside profile images on the gaming platform Steam.
The Steam platform merely serves as a vehicle which hosts the
malicious file, according to research from G Data: “The heavy lifting in
the shape of downloading, unpacking and executing a malicious payload
fetched by the loader is handled by an external component, which
accesses the malicious profile image on one Steam profile. This external
payload can be distributed via crafted emails to compromised websites.”
The steganography technique is obviously not new — but Steam profiles
being used as attacker-controlled hosting sites, is – and readers’ ears
perked up in a big way when we posted the story.
Twitch Source-Code Leak
In October, an anonymous user posted a link to a 125GB torrent on
4chan, containing all of Twitch’s source code, comments going back to
its inception, user-payout information and more.
The attacker claimed to have ransacked the live gameplay-streaming platform for everything it’s got; Twitch confirmed the breach not long after.
The threat actor rationalized gutting the service by saying that the
Twitch community needs to have the wind knocked out of its lungs. They
called the leak a means to “foster more disruption and competition in
the online-video streaming space,” because “their community is a
disgusting toxic cesspool.”
Steam-Stealing Discord Scams
In November, a scam started making the rounds on Discord, through
which cybercriminals could harvest Steam account information and make
off with any value the account contained.
Gamer-aimed Discord scams are just about everywhere. But researchers flagged a new approach
as noteworthy because it crossed over between Discord and the Stream
gaming platform, with crooks offering a purported free subscription to
Nitro (a Discord add-on that enables avatars, custom emoji, profile
badges, bigger uploads, server boosts and so on), in exchange for
“linking” the two accounts.
The target is first served a malicious direct message on Discord with
the fake offer. “Just link your Steam account and enjoy,” the message
said, which included a link to purportedly do just that. The malicious
link takes users to a spoofed Discord page with a button that reads,
“Get Nitro.” Once a victim clicks on the button, the site appears to
serve a Steam pop-up ad, but researchers explained the ad is still part
of the same malicious site.
The gambit is intended to fool users into thinking they’re being
taken to the Steam platform to enter in their login information — in
reality, the crooks are poised to harvest the credentials.
Sony PlayStation3 Bans
In June, a reported breach of a Sony folder containing the serial ID numbers for every PlayStation3 console out there appeared to have led to users being inexplicably banned from the platform.
Sony reportedly left a folder with every PS3 console ID online
unsecured, and it was discovered and reported by a Spanish YouTuber with
the handle “The WizWiki” in mid-April. In June, players on PlayStation
Network message boards began complaining that they couldn’t sign on.
Users mused that threat actors started using the stolen PS3 console
IDs for malicious purposes, causing the legitimate players to get
banned. But Sony didn’t confirm a connection between the PS3 ID breach
and player reports of being locked out of the platform.
Bonus Item: Zodiac Killer Cipher – Revealed!!
One of the quirky stories that made it into the Top 10 most-read
Threatpost stories for 2021 concerned the cracking of the Zodiac’s
serial killer’s 340 cipher, which couldn’t be solved for 50 years.
In December 2020, the code was cracked by a team of mathematicians.
The Zodiac serial killer is believed to have murdered at least five
people — and likely more — in and around the Northern California area in
the late 1960s and early 1970s. The still-unnamed murderer sent a
series of four coded messages to local newspaper outlets, bragging about
his crimes and containing cryptic icons, which earned him the moniker
“Zodiac.”
The first cipher was quickly decoded. But the second, the 340 Cipher,
named after its 340 characters, was trickier to figure out.
Australian-based mathematician Sam Blake calculated that there were
650,000 possible ways to read the code, and Jarl Van Eycke, whose day
job is as a warehouse operator in Belgium, wrote a code-breaking
software to tackle decryption. Soon, their unique algorithmic approach
paid off. The message, officially recognized by the FBI as correct,
reads:
“I HOPE YOU ARE HAVING LOTS OF FUN IN TRYING TO CATCH ME THAT WASNT
ME ON THE TV SHOW WHICH BRINGS UP A POINT ABOUT ME I AM NOT AFRAID OF
THE GAS CHAMBER BECAUSE IT WILL SEND ME TO PARADICE ALL THE SOONER
BECAUSE I NOW HAVE ENOUGH SLAVES TO WORK FOR ME WHERE EVERYONE ELSE HAS
NOTHING WHEN THEY REACH PARADICE SO THEY ARE AFRAID OF DEATH I AM NOT
AFRAID BECAUSE I KNOW THAT MY NEW LIFE IS LIFE WILL BE AN EASY ONE IN
PARADICE DEATH.”
While the name of the elusive serial killer remains hidden, the
breakthrough represents a triumph for cryptology and the basic building
blocks of cybersecurity — access control and segmentation.