Here’s how you change the title text that appears at the top of the Messenger window. By default, this is “Yahoo! Messenger”, followed by your status. Simply edit the ymsgr.ini file, which you will find in the same folder as the Messenger program, in your Program Files folder. Locate the file and open it in Notepad. Then, at the end, add the following:
[APP TITLE]
caption=YOUR TEXT
Here, “YOUR TEXT” is whatever you want in the title bar. Save the file and close Messenger. When you restart it you will see your text in the title bar.
Change The Title Of Yahoo Messenger
Email Tracking
One of most the frequently asked question is how to track an email back to the sender.That is how to determine the sender of the email? The most obvious answer is by looking at the "From:" line! But this does not work all the time since most of the spammers forge the email address or most of the spam that we get has a forged email address.This is also known as a spoofed email.Is it possible to send email from other's address?Yes it is possible to send email from anyone's name.Why not, you can send an email even from Bill Gate's Email ID.If you need a proof look here!
For more information on how to send a spoofed email refer this post.
OK now let's come back to the topic of email tracking.So how do you determine where a message actually came from?For that you have to understand how email messages are put together in order to backtrack an email message. SMTP is a text based protocol for transferring messages across the internet. A series of headers are placed in front of the data portion of the message. By examining the headers you can usually backtrack a message to the source network, sometimes the source host. A more detailed essay on reading email headers can be found .
If you are using Outlook or Outlook Express you can view the headers by right clicking on the message and selecting properties or options.
Below are listed the headers of an actual spam message.I have double spaced the headers to make them more readable.
Return-Path: <s359dyxtt@yahoo.com>
X-Original-To: sriki@example.com
Delivered-To: sriki@example.com
Received: from 12-218-172-108.client.mchsi.com (12-218-172-108.client.mchsi.com [12.218.172.108])by mailhost.example.com (Postfix) with SMTP id 1F9B8511C7for <sriki@example.com>; Sun, 16 Nov 2003 09:50:37 -0800 (PST)
Received: from (HELO 0udjou) [193.12.169.0] by 12-218-172-108.client.mchsi.com with ESMTP id <536806-74276>; Sun, 16 Nov 2003 19:42:31 +0200
Message-ID: <n5-l067n7z$46-z$-n@eo2.32574>
From: "Maricela Paulson" <s359dyxtt@yahoo.com>
Reply-To: "Maricela Paulson" <s359dyxtt@yahoo.com>
To: sriki@example.com
Subject: You Have won $10000 in US Lottery Scheme
Date: Sun, 16 Nov 2003 19:42:31 +0200
X-Mailer: Internet Mail Service (5.5.2650.21)
X-Priority: 3
MIME-Version: 1.0
Content-Type: multipart/alternative; boundary="MIMEStream=_0+211404_90873633350646_4032088448"
According to the From header this message is from Maricela Paulson at s359dyxxt@yahoo.com. I could just fire off a message to abuse@yahoo.com, but that would be waste of time. This message didn't come from yahoo's email service.
The header most likely to be useful in determining the actual source of an email message is the Received header. According to the top-most Received header this message was received from the host 12-218-172-108.client.mchsi.com with the ip address of 21.218.172.108 by my server mailhost.example.com. An important item to consider is at what point in the chain does the email system become untrusted? I consider anything beyond my own email server to be an unreliable source of information. Because this header was generated by my email server it is reasonable for me to accept it at face value.
The next Received header (which is chronologically the first) shows the remote email server accepting the message from the host 0udjou with the ip 193.12.169.0. Those of you who know anything about IP will realize that that is not a valid host IP address. In addition, any hostname that ends in client.mchsi.com is unlikely to be an authorized email server. This has every sign of being a cracked client system.
Here's is where we start digging. By default Windows is somewhat lacking in network diagnostic tools; however, you can use the tools at to do your own checking.
sriki@nqh9k:[/home/sriki] $whois 12.218.172.108 AT&T WorldNet Services ATT (NET-12-0-0-0-1)12.0.0.0 - 12.255.255.255Mediacom Communications Corp MEDIACOMCC-12-218-168-0-FLANDREAU-MN (NET-12-218-168-0-1)12.218.168.0 - 12.218.175.255
# ARIN WHOIS database, last updated 2003-12-31 19:15# Enter ? for additional hints on searching ARIN's WHOIS database.
I can also verify the hostname of the remote server by using nslookup, although in this particular instance, my email server has already provided both the IP address and the hostname.
sriki@nqh9k:[/home/sriki] $nslookup 12.218.172.108
Server: localhostAddress: 127.0.0.1
Name: 12-218-172-108.client.mchsi.comAddress: 12.218.172.108
Ok, whois shows that Mediacom Communications owns that netblock and nslookup confirms the address to hostname mapping of the remote server,12-218-172-108.client.mchsi.com. If I preface a www in front of the domain name portion and plug that into my web browser, http://www.mchsi.com/, I get Mediacom's web site.
There are few things more embarrassing to me than firing off an angry message to someone who is supposedly responsible for a problem, and being wrong. By double checking who owns the remote host's IP address using two different tools (whois and nslookup) I minimize the chance of making myself look like an idiot.
A quick glance at the web site and it appears they are an ISP. Now if I copy the entire message including the headers into a new email message and send it to abuse@mchsi.com with a short message explaining the situation, they may do something about it.
But what about Maricela Paulson? There really is no way to determine who sent a message, the best you can hope for is to find out what host sent it. Even in the case of a PGP signed messages there is no guarantee that one particular person actually pressed the send button. Obviously determining who the actual sender of an email message is much more involved than reading the From header. Hopefully this example may be of some use to other forum regulars.
Change IP Address
How to change your IP address in less than a minute? The following trick gives you a step-by-step procedure to change your IP address.
1. Click on "Start" in the bottom left hand corner of screen.
2. Click on "Run".
3. Type in "command" and hit ok.You should now be at an MSDOS prompt screen.
4. Type "ipconfig /release" just like that, and hit "enter".
5. Type "exit" and leave the prompt.
6. Right-click on "Network Places" or "My Network Places" on your desktop.
7. Click on "properties".
You should now be on a screen with something titled "Local Area Connection", or something close to that.
8. Right click on "Local Area Connection" and click "properties".
9. Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab.
10. Click on "Use the following IP address" under the "General" tab.
11. Create an IP address (It doesn't matter what it is. I just type 1 and 2 until i fill the area up).
12. Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
13. Hit the "Ok" button here.
14. Hit the "Ok" button again.You should now be back to the "Local Area Connection" screen.
15. Right-click back on "Local Area Connection" and go to properties again.
16. Go back to the "TCP/IP" settings.
17. This time, select "Obtain an IP address automatically".
18. Hit "Ok".
19. Hit "Ok" again.
20. You now have a new IP address.
Some ISPs do not support this type of procedure and hence there are chances of getting back the same old IP address even after trying this hack.In this case you need to switch off the modem and then switch it on to get the new IP address.
NOTE: All these tricks works only if you have a dynamic IP address.But if you have a static IP address you have no option to change your IP.
How To Disable Windows Logo Key?
At times it becomes necessary to disable the Windows Key on the keyboard.For example when playing games this nasty Windows Logo key keeps annoying , as we often accidently press it and this takes our game out to the desktop.So it becomes necessary to disable it when not needed an re-enable it when needed.
The following download consists of two registry scripts (.reg) one to disable windows key and the other to re-enable it.In this download there are two files
disable_winlogo_key.reg - Disable Windows Logo Ley
re-enable_winlogo_key.reg - Re-Enable Windows Logo Key
DOWNLOAD
Windows XP IP Utilities
The following are the IP utilities available in Windows that help in finding out the information about IP Hosts and domains.These are the basic IP Hacking Commands that everyone must know!
NOTE: The term Host used in this article can also be assumed as a Website for simple understanding purpose.
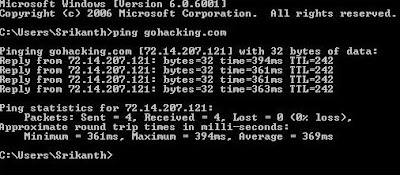
1. PING
PING is a simple application (command) used to determine whether a host is online and available.PING command sends one or more ICMP Echo messages to a specified host requesting a reply.The receiver (Target Host) responds to this ICMP Echo message and returns it back to the sender.This confirms that the Host is online and available.Otherwise the host is said to be unavailable.
Syntax:
C:\>ping gohacking.com
The following image shows the ping command which pings the host gohacking.com
2. TELNET
Telnet command is used to connect to a desired host on a specified port number.For example
Syntax:
C:\>telnet yahoo.com 25
C:\>telnet yahoo.com
NOTE: The default port number is 23.When the port number is not specified the default number is assumed.
Telnet Hacking is explained in detail in the following post.
How To Send Fake Email
3. NSLOOKUP
Many times we think about finding out the IP address of a given site.Say for example google.com,yahoo.com,microsoft.com etc.But how to do this? For this there are some websites that can be used to find out the IP address of a given site.But in Windows we have an inbuilt tool to do this job for us.It is nslookup.Yes this tool can be used for resolving a given domain name into it's IP address (determine the IP of a given site name).Not only this it can also be used for reverse IP lookup.That is if the IP address is given it determines the corresponding domain name for that IP address.
Syntax:
C:\>nslookup google.com
The following images shows the usage of nslookup command.
4. NETSTAT
The netstat command can be used to display the current TCP/IP network connections.For example the following netstat command displays all connections and their corresponding listening port numbers.
Eg: C:\>netstat -a
This command can be used to determine the IP address/Host names of all the applications connected to your computer.If a hacker is connected to your system even the hacker's IP is displayed.So the netstat command can be used to get an idea of all the active connections to a given system.
Password Hacking
1. What are some password basics?
Most accounts on a computer system usually have some method of restricting access to that account, usually in the form of a password. When accessing the system, the user has to present a valid ID to use the system, followed by a password to use the account. Most systems either do not echo the password back on the screen as it is typed, or they print an asterisk in place of the real character.
On most systems,the password is typically ran through some type of algorithm to generate a hash. The hash is usually more than just a scrambled version of the original text that made up the password, it is usually a one-way hash. The one-way hash is a string of characters that cannot be reversed into its original text. You see, most systems do not "decrypt" the stored password during authentication, they store the one-way hash. During the login process, you supply an account and password. The password is ran through an algorithm that generates a one-way hash. This hash is compared to the hash stored on the system. If they are the same, it is assumed the proper password was supplied.
Cryptographically speaking, some algorithms are better than others at generating a one-way hash. The main operating systems we are covering here -- NT, Netware, and Unix -- all use an algorithm that has been made publically available and has been scrutinized to some degree.
To crack a password requires getting a copy of the one-way hash stored on the server, and then using the algorithm generate your own hash until you get a match. When you get a match, whatever word you used to generate your hash will allow you to log into that system. Since this can be rather time-consuming, automation is typically used. There are freeware password crackers available for NT, Netware, and Unix.
2. Why protect the hashes?
If the one-way hashes are not the password itself but a mathematical derivative, why should they be protected? Well, since the algorithm is already known, a password cracker could be used to simply encrypt the possible passwords and compare the one-way hashes until you get a match. There are two types of approaches to this -- dictionary and brute force.
Usually the hashes are stored in a part of the system that has extra security to limit access from potential crackers.
3. What is a dictionary password cracker?
A dictionary password cracker simply takes a list of dictionary words, and one at a time encrypts them to see if they encrypt to the one way hash from the system. If the hashes are equal, the password is considered cracked, and the word tried from the dictionary list is the password.
Some of these dictionary crackers can "manipulate" each word in the wordlist by using filters. These rules/filters allow you to change "idiot" to "1d10t" and other advanced variations to get the most from a word list. The best known of these mutation filters are the rules that come with Crack (for Unix). These filtering rules are so popular they have been ported over to cracking software for NT.
If your dictionary cracker does not have manipulation rules, you can "pre-treat" the wordlist. There are plenty of wordlist manipulation tools that allow all kinds of ways to filter, expand, and alter wordlists. With a little careful planning, you can turn a small collection of wordlists into a very large and thorough list for dictionary crackers without those fancy word manipulations built in.
4. What is a brute force password cracker?
A brute force cracker simply tries all possible passwords until it gets the password. From a cracker perspective, this is usually very time consuming. However, given enough time and CPU power, the password eventually gets cracked.
Most modern brute force crackers allow a number of options to be specified, such as maximum password length or characters to brute force with.
5. Which method is best for cracking?
It really depends on your goal, the cracking software you have, and the operating system you are trying to crack. Let's go through several scenarios.
If you remotely retrieved the password file through some system bug, your goal may be to simply get logged into that system. With the password file, you now have the user accounts and the hashes. A dictionary attack seems like the quickest method, as you may simply want access to the box. This is typical if you have a method of leveraging basic access to gain god status.
If you already have basic access and used this access to get the password file, maybe you have a particular account you wish to crack. While a couple of swipes with a dictionary cracker might help, brute force may be the way to go.
If your cracking software does both dictionary and brute force, and both are quite slow, you may just wish to kick off a brute force attack and then go about your day. By all means, we recommend a dictionary attack with a pre-treated wordlist first, followed up by brute force only on the accounts you really want the password to.
You should pre-treat your wordlists if the machine you are going to be cracking from bottlenecks more at the CPU than at the disk controller. For example, some slower computers with extremely fast drives make good candidates for large pre-treated wordlists, but if you have the CPU cycles to spare you might want to let the cracking program's manipulation filters do their thing.
A lot of serious hackers have a large wordlist in both regular and pre-treated form to accommodate either need.
6. What is a salt?
To increase the overhead in cracking passwords, some algorithms employ salts to add further complexity and difficulty to the cracking of passwords. These salts are typically 2 to 8 bytes in length, and algorithmically introduced to further obfuscate the one-way hash. Of the major operating systems covered here, only NT does not use a salt. The specifics for salts for both Unix and Netware systems are covered in their individual password sections.
Historically, the way cracking has been done is to take a potential password, encrypt it and produce the hash, and then compare the result to each account in the password file. By adding a salt, you force the cracker to have to read the salt in and encrypt the potential password with each salt present in the password file. This increases the amount of time to break all of the passwords, although it is certainly no guarantee that the passwords can't be cracked. Because of this most modern password crackers when dealing with salts do give the option of checking a specific account.
7. What are the dangers of cracking passwords?
The dangers are quite simple, and quite real. If you are caught with a password file you do not have legitimate access to, you are technically in possession of stolen property in the eyes of the law. For this reason, some hackers like to run the cracking on someone else's systems, thereby limiting their liability. I would only recommend doing this on a system you have a legitimate or well-established account on if you wish to keep a good eye on things, but perhaps have a way of running the cracking software under a different account than your own. This way, if the cracking is discovered (as it often is -- cracking is fairly CPU-intensive), it looks to belong to someone else. Obviously, you would want to run this under system adminstrator priviledges as you may have a bit more control, such as assigning lower priority to the cracking software, and hiding the results (making it less obvious to the real administrator).
Being on a system you have legit access to also allows you better access to check on the progress. Of course, if it is known you are a hacker, you'll still be the first to be blamed whether the cracking software is yours or not!
Running the cracking software in the privacy of your own home has the advantage of allowing you to throw any and all computing power you have at your disposal at a password, but if caught (say you get raided) then there is little doubt whose cracking job is running. However, there are a couple of things you can do to protect yourself: encrypt your files. Only decrypt them when you are viewing them, and wipe and/or encrypt them back after you are done viewing them.
8. Is there any way I can open a password-protected Microsoft Office document?
Certainly! There are plenty of commercial programs that will do this, but we give props to Elcomsoft for fighting the DMCA. 30-day trial versions are available here
BlazingTools Perfect Keylogger Lite (Keylogger)
BlazingTools Perfect Keylogger Lite:
Description:
Do you want to know what your buddy or colleague is typing? May be you want to control your family members - what are they doing on your computer? Some applications of the keylogger: - Monitor children's activity for parents - Monitor what programs opened and when - Recall what you wrote some time ago - Special purposes Features: - Invisible in Task Manager List - Logging texts typed in every application (including passwords and other hidden texts) - Log file is encrypted and can be protected with a password - Easy log viewing and management - Export log to HTML format - Possibility to specify target applications - Supports all Windows versions, including Windows XP - Very easy to use - Free version.
Download










