Keyboard Spectator Free
Description:
Keyboard Spectator is a multifunctional keyboard tracking software (a.k.a. key logger) that is widely used by both regular users and IT security specialists. The reason for such popularity is that this program does not just record keystrokes; it is capable of recording language specific characters (ex. umlauts), date and time certain window was initiated as well as the caption of that window. Thus, this software combines two very important qualities - it records all typed data, so that you won't lose it when your computer unexpectedly crashes, and it keeps the record of all keyboard activity. It allows you to monitor your children's activity at home or to make sure your employees do not use company's computers inappropriately.
Download
Keyboard Spectator Free (Keylogger)
Ardamax Keylogger Lite (Keylogger)
Ardamax Keylogger Lite
Description
Ardamax Keylogger Lite is a small, freeware keylogger that captures users activity and saves it to a logfile. The logfile can be viewed as a text or web page. Use this tool to find out what is happening on your computer while your away, maintain a backup of your typed data automatically or use it to monitor your kids.
Download
Quick Keylogger (Keylogger)
Quick Keylogger
Description
WideStep Software presents light and affordable monitoring utility Quick Keylogger that supports 64 bit Windows as well as other OS. Simple download and deployment guarantees a smooth start of your work with the optimal set of features: keystrokes, websites and other monitoring options. Simple but clear HTML reports make Quick Keylogger a great solution for everyone. Quick Keylogger will save keystrokes by application, date and time, it will capture absolutely all keystrokes, all buttons pressed in your system. Unfortunately unlike Elite Keylogger it is not that invisible to anti-keyloggers and anti-viruses. Designed for Windows 9x, Windows XP and Windows Vista Quick Keylogger offers you stability and simplicity with the most usable number of features. Quick Keylogger works seemlessly in the background and you are the only one who knows the password to view the logs. Quick Keylogger is equipped with a calendar that lets you sort and review logs by specific dates and time. All recorded sessions are combined by user, date, month, and time. Quick Keylogger is easy-to-use, very simple and small (instant free download) tool, which you can carry on a floppy disk drive for your mobility and fast response.
Download
Hack BSNL Broadband For Speed
If you are a BSNL broadband user, chances are that you are facing DNS issues for the last few weeks or so. Their DNS servers are just unresponsive. The lookup takes a long duration and many times just time out. The solution? Use third party DNS servers or run your own one like djbdns. The easiest options is to use OpenDNS. Just reconfigure your network to use the following DNS servers:
208.67.222.222
208.67.220.220
Detailed instructions specific to your router are available in the OpenDNS website itself. After I reconfigured my Linksys router to use the above 2 IP addresses, my DNS problems just vanished! Other ‘freebies’ that come with OpenDNS are phishing filters and automatic URL correction. Even if your service provider’s DNS servers are working fine, you can still use OpenDNS just for these two special features.
Bypassing Vista SP1 Windows Genuine Advantage
The fact that Microsoft has relaxed its antipiracy mechanism built into Windows Vista concomitantly with the release of Service Pack 1 failed to stop hackers from providing a crack for the latest version of Windows Genuine Advantage Validation.
Various reports point out that Genuine Advantage Validation and Notifications versions 1.7.69.1 (1.7.0069.1) and 1.7.69.2 released in March 2008, following the March 18 availability of Windows Vista SP1 through Windows Update and the Microsoft Download Center, have been cracked.
The workaround is designed to be integrated with pirated copies of Windows XP and Windows Vista in order to render useless the WGA Validation mechanism. According to the reports, applying the WGA crack will permit users of counterfeit versions of Windows to access and download items from Windows Update, Microsoft Download Center and Microsoft Update. The pirated operating systems with the cracked WGA will pass all validations on Microsoft's websites and offer anything from updates to applications that are restricted to users of genuine operating systems only.
With the release of Windows Vista SP1, Microsoft has scrapped the Reduced Functionality Mode kill switch in its latest operating system. Users of pirated Vista, just as those of XP and Windows Server 2008 will only be informed of the fact that their operating system is no longer genuine. However, pirated versions of Windows are automatically blocked from downloading certain free applications as well as all updates except those labeled Critical. The WGA crack is designed to fix that.
"After the activation grace period has been exceeded the next logon will present the user with a message that directs the customer to activate that copy of Windows. That dialog includes a fifteen second delay before it can be dismissed. If they want to skip activation at that time they can wait for the fifteen seconds and choose "Activate Later" .
But the new story is different.That is Vista SP1 has been cracked successfully and it's possible to bypass the Windows Genuine Advantage to fool the OS to beleive it as genuine.The release of Service Pack 1 for Vista seems to put no combat against piracy.This crack is available for download on this site.
MORE INFORMATION ON THE CRACK(ACTIVATOR)
VistaSP1_1-Click Activator
Unlike the other cracks eg: Vista Loader 3.0.0.1(which has some known issues with dual booting systems) this crack has been designed to work on dual booting systems.
This crack has incorporated an automated installation process which makes it easy to install.You can select from 4 OEM Logos and licenses during installation and within a few seconds your copy will be activated.You can see the system activated upon restart.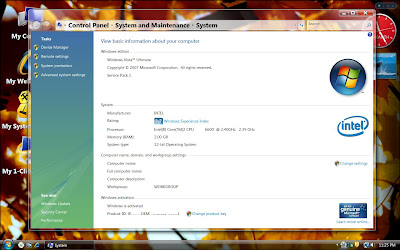
This crack also features the uninstallation process which most of the cracks lack the same.Using this is not necessary to carry out the manual uninstallation process.You can just uninstall the crack with a single click.
PLEASE FOLLOW THESE INSTRUCTIONS BEFORE APPLYING THIS CRACK.
1.YOU MUST HAVE FULL ADMINISTRATOR RIGHTS TO INSTALL THIS CRACK.
2.TURN OFF USER ACCOUNT CONTROL(UAC) BEFORE INSTALLING THIS CRACK.
3.THIS CRACK CURRENTLY WORKS ONLY WITH 32-BIT ULTIMATE EDITION OF WINDOWS VISTA.
4.EASY ONE CLICK ACTIVATOR.
5.YOU CAN ALSO USE THIS CRACK TO UNINSTALL THE ACTIVATOR.
ENJOY!!!
Here is the download link for the crack
DOWNLOAD
Please post your feedback through comments.
A File Embedder Project In C
Some times it is necessary for our compiled project to have it's supporting files embedded within the EXE module itself so that the supporting files may not be put into a seperate folder and carried along with the project.So here i am presenting you with the source code of the FILE EMBEDDER UTILITY project.
This utility can be used to embed one file with in the other.ie:Suppose we need to embed a .bat file(or any other file *.exe,*bmp,.txt.....) into our final project so that the batch file is present with in the compiled module and is hidden from the users avoiding tthe need to carry the .bat file every time with the project.
Both the Embedding and extraction process has been presented in seperate functions for your convenience.here's the code.....
#include<stdio.h>
#include<conio.h>
#include<fcntl.h>
#include<sys/types.h>
#include<sys/stat.h>
#include<stdlib.h>
#include<string.h>
void embed(void);
void extract(void);
char buff[1],sname[128],tname[128],dname[128],choice;
unsigned long int size=0;long int psize=0;int outh,bytes=0;
FILE *source,*target,*data;
void main()
{
while(1)
{
clrscr();
puts("\n\n\t\t\tFILE EMBEDDING UTILITY BY SRIKANTH\n\n\n");
puts("1.Embed A File 2. Extract A File 3.Exit\n");
choice=getch();
switch(choice)
{
case '1':embed();
getch();
break;
case '2':
extract();
getch();
break;
default:
exit(0);
}
}
}
void embed()
{
puts("\nEnter The Source Filename\n");
scanf("%s",sname);
source=fopen(sname,"rb+");
if(source==NULL)
{
puts("\nCannot Open The Source File\n");
return;
}
puts("\nEnter The Target Filename\n");
scanf("%s",tname);
outh=open(tname,O_RDONLYO_BINARY);
if(outh==-1)
{
puts("\nCannot Open The Target File\n");
return;
}
printf("\nReading The Source File Please Wait...\n");
while((bytes=read(outh,buff,1))>0)
size+=bytes;
data=fopen("Data.cfg","w");
if(data==NULL)
{
puts("\nCannot Create Configuration The File\n");
return;
}
fprintf(data,"%lu",size);
close(outh);
fclose(data);
target=fopen(tname,"rb");
if(target==NULL)
{
puts("Cannot Open Target File\n");
return;
}
printf("\nEmbedding Please Wait...\n");
fseek(source,0,SEEK_END);
while(fread(buff,1,1,target)>0)
fwrite(buff,1,1,source);
fcloseall();
printf("\nEmbedding Completed Successfully\n");
}
void extract()
{
printf("\nEnter The Source Filename\n");
scanf("%s",sname);
source=fopen(sname,"rb");
if(source==NULL)
{
printf("\nCannot Open The Source File\n");
return;
}
printf("\nEnter The Target Filename(eg: abc.exe)\n");
scanf("%s",tname);
printf("\nEnter The Configuration Filename(eg: DATA.cfg)\n");
scanf("%s",dname);
data=fopen(dname,"r");
if(data==NULL)
{
printf("\nConfiguration File Not Found\n");
return;
}
fscanf(data,"%ld",&psize);
target=fopen(tname,"wb");
if(target==NULL)
{
puts("\nCannot Open The Target File\n");
return;
}
printf("\nExtracting Please Wait...\n");
fseek(source,-psize,SEEK_END);
while((fread(buff,1,1,source))>0)
fwrite(buff,1,1,target);
printf("\nFile Extraction Completed Successfully\n");
fcloseall();
}
YOU CAN DOWNLOAD THE COMPILED MODULE OF THE ABOVE CODE HERE
Please pass your feedback through comments...........
Program To Hack Yahoo Accounts
There are number of sites which provide information about hacking email accounts.So what's special about this site? The only special about this site is that we do not bluff and mislead readers.We actually teach you how to track someone's email password rather than telling some nosense tricks to hack or crack someone's email.
One thing i'll make clear.There is no program that is particularly meant for hacking some one's email password.But it is still possible to sniff the password of the victim using some tools called Keyloggers OR Remote administration tools.For more information on Keyloggers refer this page.
I'll not elaborate this post since i have already discussed about- How to hack an email account.So this post is an addon to my previous post.Here i am giving information on two new programs that can be used to hack some one's email password or any other information "REMOTELY".You need not have physical accress to the victims PC.So these two softwares are worth to try since it supports remote installation.The following are the two new programs...
1.Remote Logger
Remote Logger Features:
Remote Installation - lets you to create a customized Remote Logger engine file. You can send this file to your target for remote monitoring.
Stealth mode
Very small size - Remote Logger is the smallest keylogger available!
Invisible mode - Remote Logger is invisible in the task bar, system tray, Windows 98/2000/XP/2003/Vista Task Manager, Start Menu and Windows Startup list.
Password capture - Remote Logger invisibly captures and records all passwords.
Email log delivery - log files can be invisibly emailed to you.
FTP Delivery - Remote Logger can upload recorded logs on the FTP server.
Keystroke logging and application monitoring - keylogger will record all keystrokes typed and all applications launched!
Unicode engine supports virtually all input languages, including Chinese, Japanese, Thai etc. Most competitive keyloggers record english keystrokes only.
Website logging - supports all popular browsers
Chat logging - supports all popular instant messengers
Screenshot recording
Powerful Log Viewer - offers an easy navigation through the log files.
Multi user support - Remote Logger can monitor all users of the PC.
Windows 98/NT/2000/XP/2003/Vista support
Friendly and easy to use user interface - even for novices!
2.SuperKeylogger
Superkeylogger features :
This program allows you to remotely install the monitoring system through an email attachment (no physical installation needed) without the user recognizing theinstallation at all.
User can set number of days in remote installation package after which Superkeylogger will uninstall itself automatically. (New)
User definable Server Name for remote installation package. (New)
No SMTP server required to send log mails.
Records applications activity showing you which programs were launched.
Records absolutely all keystrokes, including system keys.
Records all passwords, including passwords to e-mails and websites, etc.
Log both side Chat (Yahoo Messenger / Msn Messenger). (New)
Monitors Internet activity, websites and web-pages visited.
Captures all e-mails sent on monitored PC, no matter if it is Outlook or any other e-mail client, or the mail is sent using web-interface.
Records desktop activity by taking snapshots of your desktop at a customizable interval.
Unique un-hiding mechanism - you can choose any secret word to unhide the Super key logger.
Simple installation/un-installation - suitable for all users
Automatically & Invisibly send logs to predefined email address on customizable intervals.
Automatically & invisibly send logs to any predefined FTP address. (New)
Automatically removal of already emailed log files.
Extremely low system requirements.
Absolutely invisible.
Each entry in the log is accompanied by detailed information (time, date, username, application, etc)
Monitors all users on your PC.
Easily configurable.
Automatic startup with system startup.
Thse two softwares are none other than keyloggers but supports remote installation..










